Android 01
This exercise will guide through the process of extracting simple information from an APK
Getting the Android application
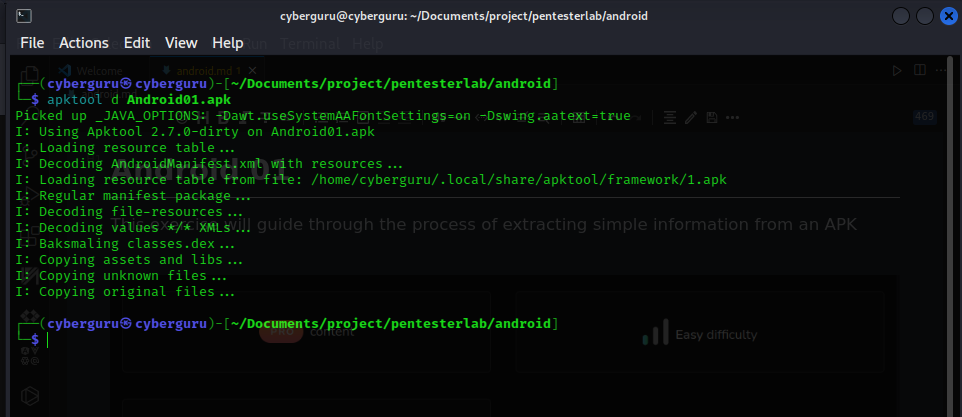
In this challenge, we download the Android application using the following link: Android01.apk then we use apktool to decompile it using the following command:
apktool d Andriod01
and got the following result:
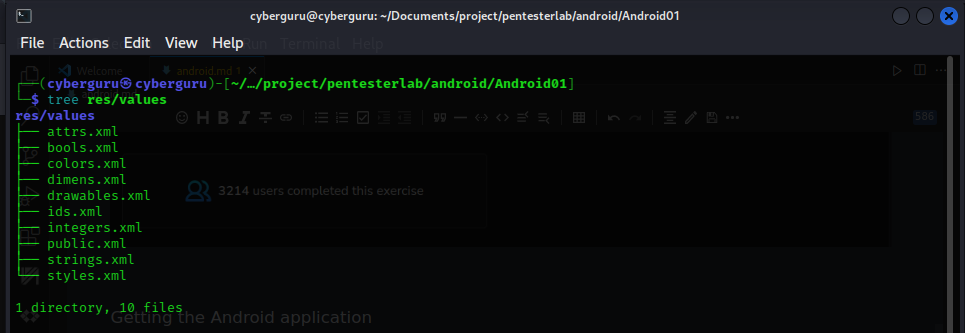
we navigate to the res/values/strings.xml and got the pt_key to the lab
Android 02
This exercise will guide through the process of extracting data from a simple database used by an Android app
As in the previous challenge we download the file and extract it using apktool then search for a file relating to a db or sqlite db file:
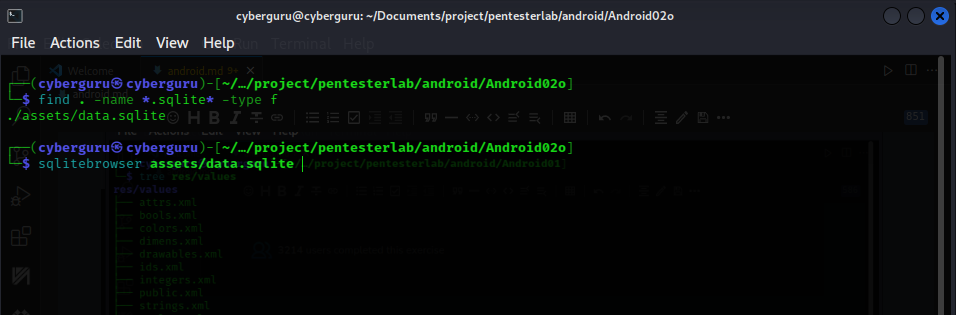
we then use sqlite browser to open the file:
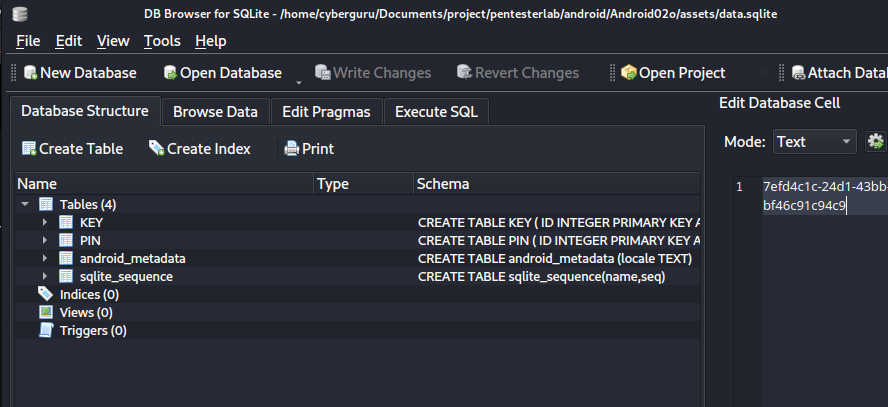
This shows us the key!!!!!!!
Android 03
This exercise will guide through the process of extracting simple information from an APK
This challenge is simillar with the previous levels; but this case as to do with reviewing the source code of the main app itself.
we first of all unzip the file and used dex2jar to turn the *.dex file to a java class file we can easily read using the following command:
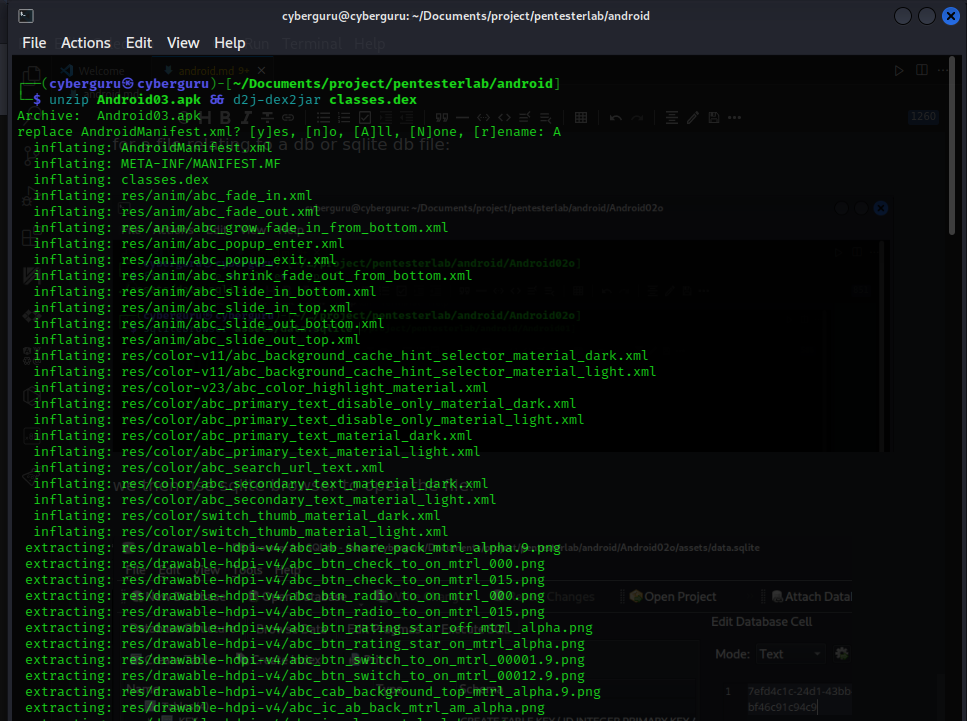
result of dex2jar:
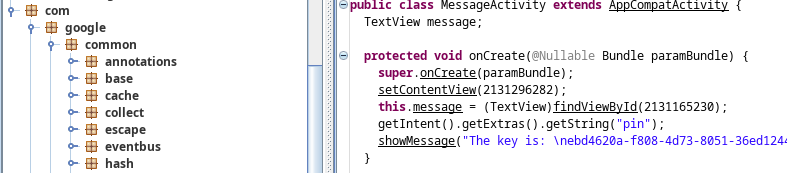
we navigate to the pentesterlab.android03 class section and go to messageActivity.class file

and the code is right there :
Android 04
This exercise will guide through the process of reversing simple Android code
We do the same step as lab 03 and get the source code then examine it, we saw the code that encrypts and decrypts the key value:
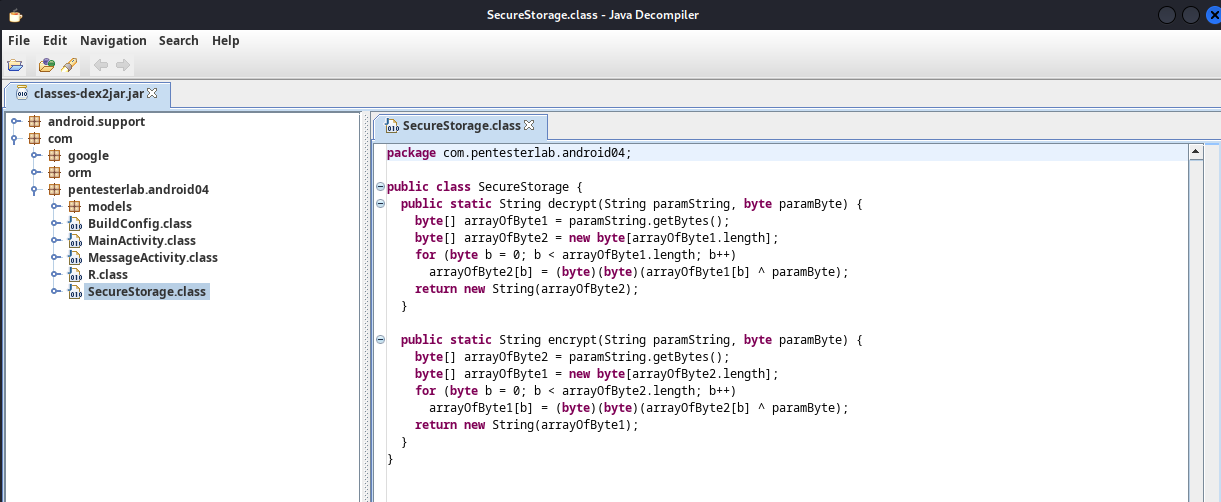
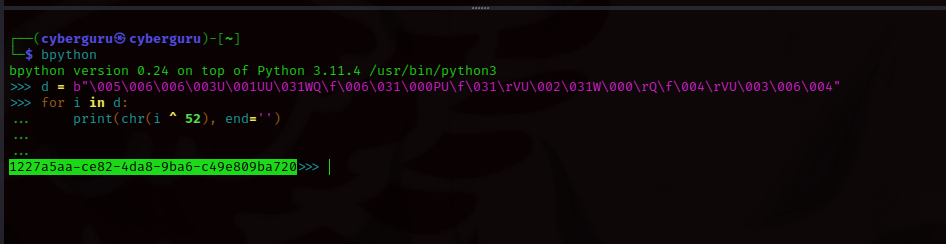
in the graphic below, we could see the encrypted key being passed to a decryption function with the xor key 52 to be decoded:

we replicate this using python and got our key:
Android 05
This exercise will guide through the process of reversing simple obfuscated Android code
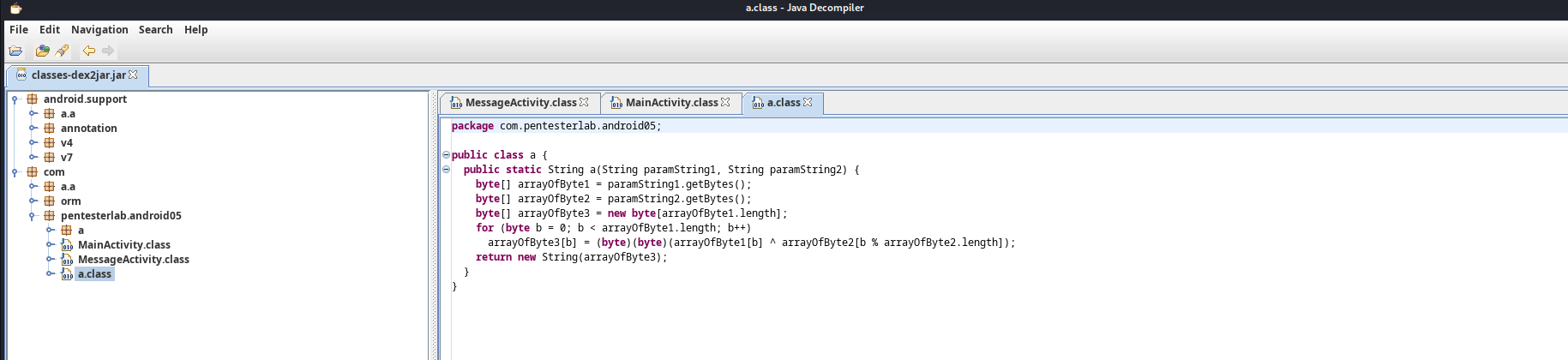
We do the usual step of extracting the source code and we have this:
This here is the code that encrypts the key:
This is our target encrypted key we need to decode:
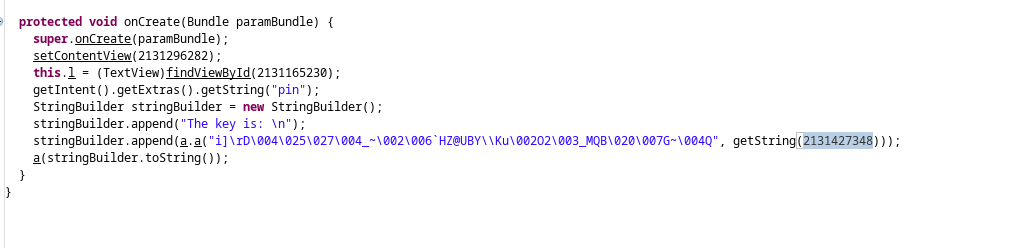
we take note of the getString(2131427348) function and the number that calls the key stored some where:
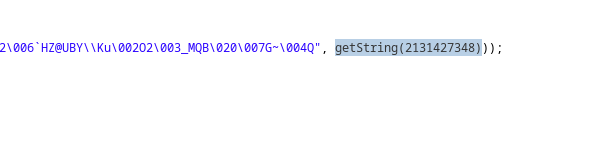
our next step is to find the content of that value and use it to decrypt our key, to do that we need to convert it to hex and search for it int the apktook decoded file using the following steps:
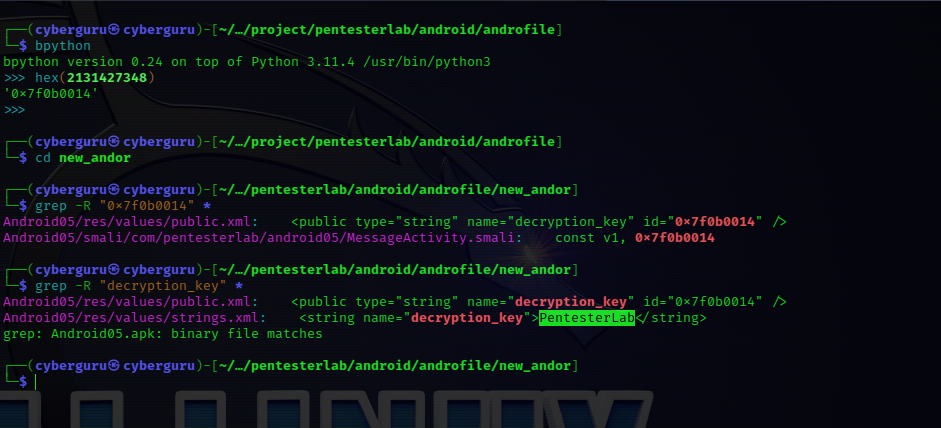
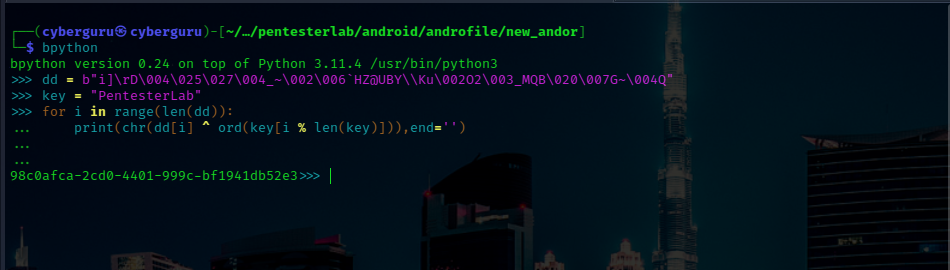
we got the decryption key to be “pentersterLab” and use it to decrypt by key-length-safe xoring it:
Android 06
This exercise will guide through the process of reversing simple obfuscated Android code
We do as usual, try to extract the source code and got here:
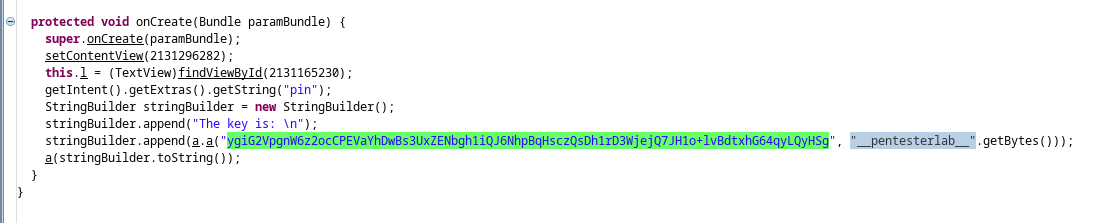
in the above graphic we could see the encrypted key and keycode passed to the function below:
public class a {
public static String a(String paramString, byte[] paramArrayOfbyte) {
try {
byte[] arrayOfByte2 = Base64.decode(paramString, 0);
byte[] arrayOfByte1 = new byte[arrayOfByte2.length];
byte[] arrayOfByte3 = new byte[16];
System.arraycopy(arrayOfByte2, 0, arrayOfByte3, 0, arrayOfByte3.length);
IvParameterSpec ivParameterSpec = new IvParameterSpec();
this(arrayOfByte3);
int i = arrayOfByte2.length - 16;
arrayOfByte3 = new byte[i];
System.arraycopy(arrayOfByte2, 16, arrayOfByte3, 0, i);
SecretKeySpec secretKeySpec = new SecretKeySpec();
this(paramArrayOfbyte, "AES");
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS5Padding");
cipher.init(2, secretKeySpec, ivParameterSpec);
return new String(cipher.doFinal(arrayOfByte3));
} catch (Exception exception) {
return "";
}
}
}
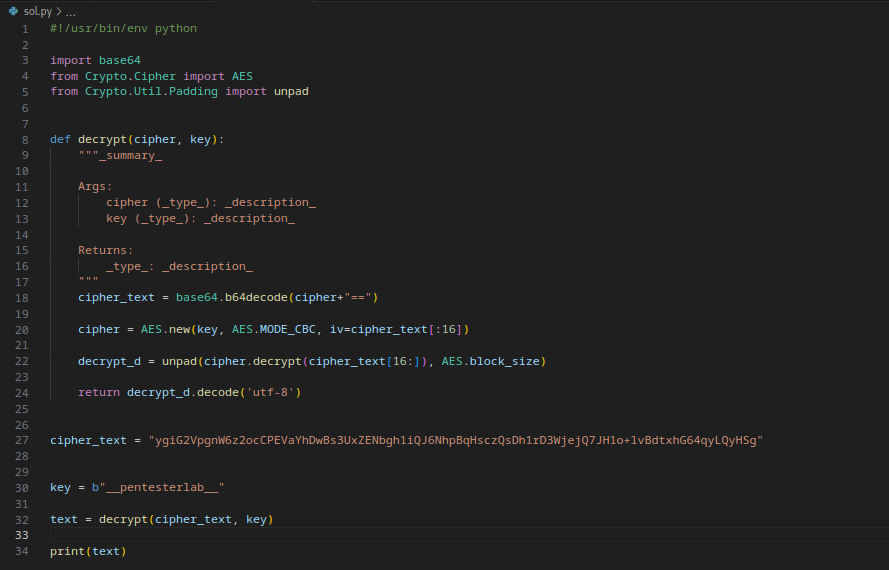
we replicate this code in python and solve the lab:
This code is an implementation of AES in CBC mode
we run the code and got the key 🎉️
Android 07
This exercise will guide through the process of reversing simple obfuscated Android code
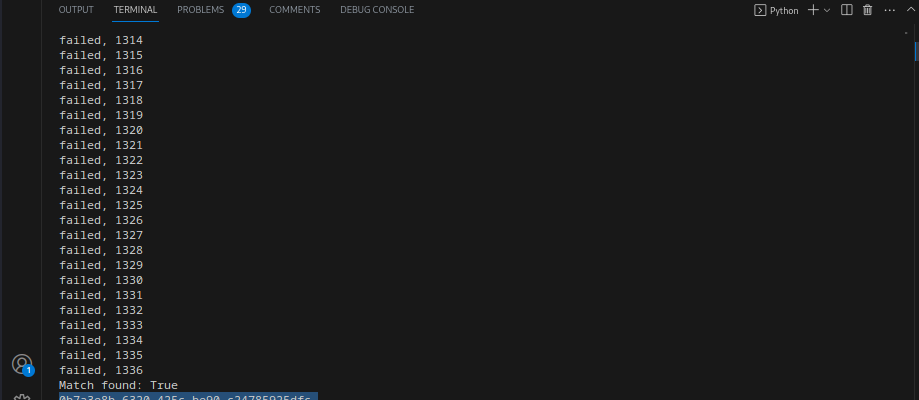
this challenge is simillar to the previous lab but in this case we need to predict the 4 digits used to encrypt the key as shown in the code:
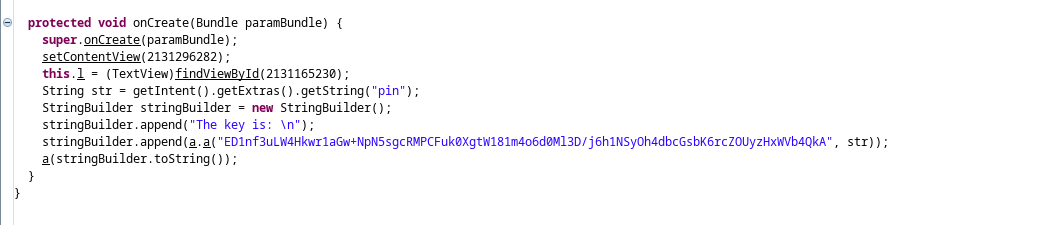
we brute force this code and run it in the previous labs code and got our key:
Android 08
This exercise will guide through the process of reversing simple obfuscated Android code to recover encrypted data
This lab is simillar to Android 7, in this case the key used for the AES encryption is a combination of a key retrived from the internet and a random 4 digit number we would have to bruteforce.
We search through the android source code in jd-gui and found a retrival lind which was used, we use wget to get this key file:
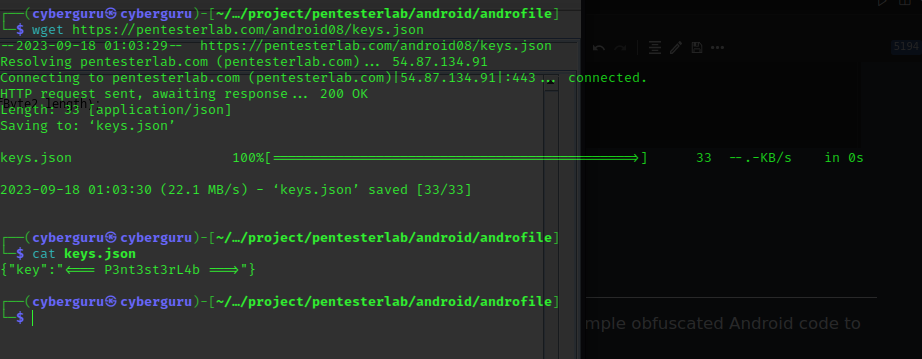
after we obtained the key we runned it with the decryption script from Android 7 and got our key after some minutes:

With this we are done with the Android lab in pentesterLab Thanks for following!!!!