Recon 00
This exercise covers the robots.txt file
Objective
For this challenge, your goal is to retrieve the robots.txt from the main website for hackycorp.com.
we solve this lab by navigating to /robots.txt on the site
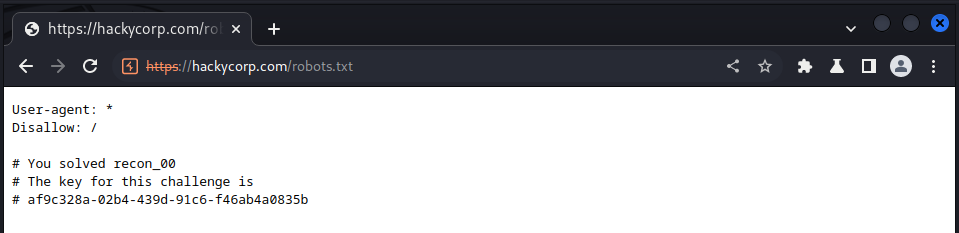
and we got our key!!!
Recon 01
This exercise covers 404 error pages
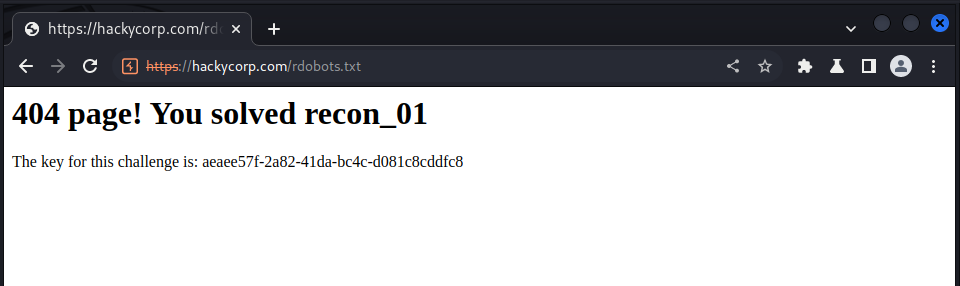
we solve this lab by accessing a path that does not exist:
Recon 02
This exercise covers the security.txt file
Objective
For this challenge, your goal is to retrieve the security.txt from the main website for hackycorp.com.
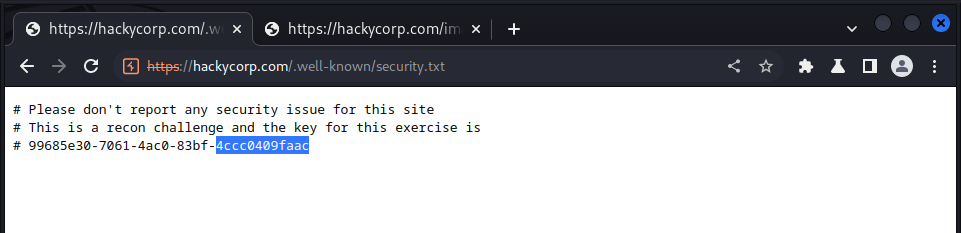
To solve this challenge we navigate to this link to check the security content:
https://hackycorp.com/.well-known/security.txt
and we get the key:
Recon 03
This exercise covers directory listing
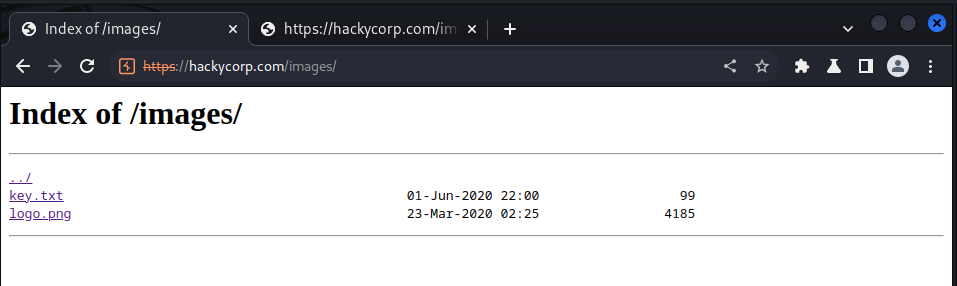
we navigate to the images’ directory of the site and got this
we now try accessing the key.txt file:
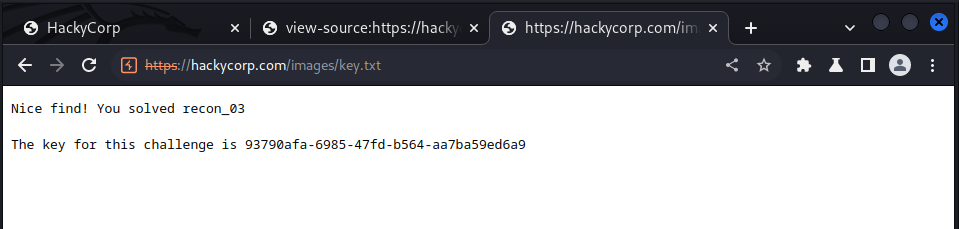
and we got our key!!!
Recon 04
This exercise covers common interesting directories
Objective
For this challenge, your goal is to find a directory that is commonly used to manage applications.
we sovle this lab by accessing the /admin endpoint, and we got this:
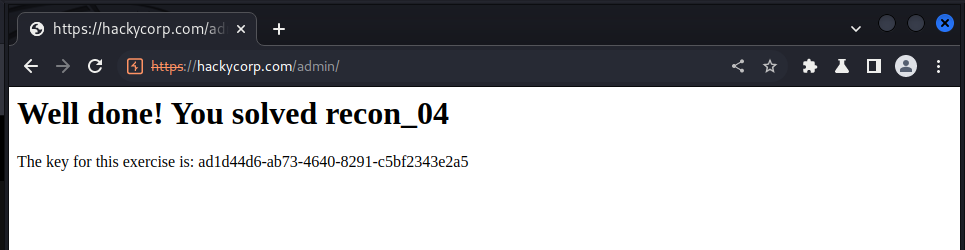
Recon 05
This exercise covers simple directory brute forcing
Objective
For this challenge, your goal is to find a directory that is not directly accessible.
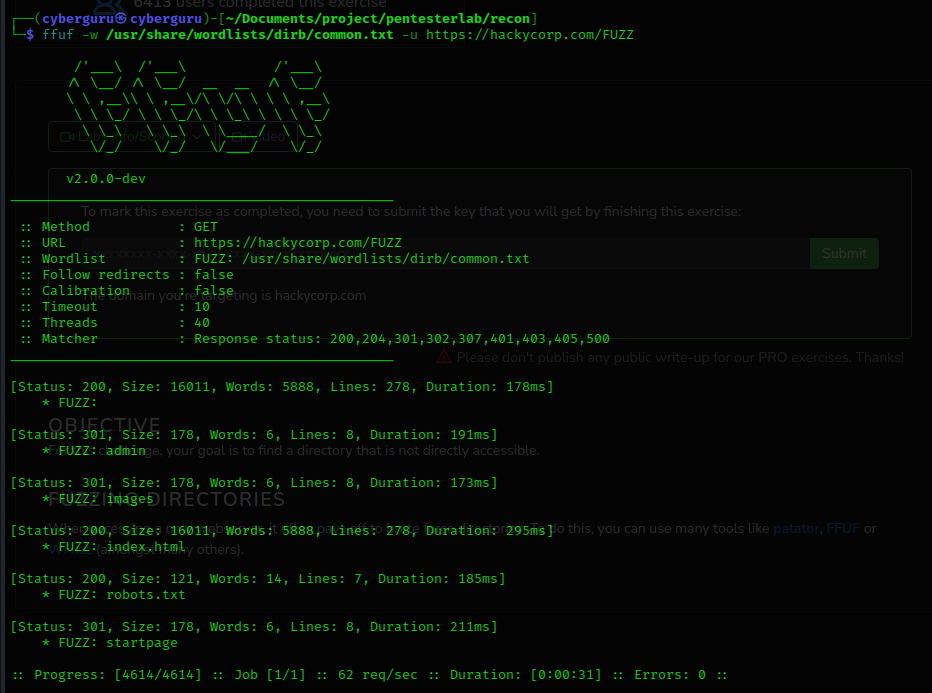
we used ffuf to perform directory brute force and got the following result:
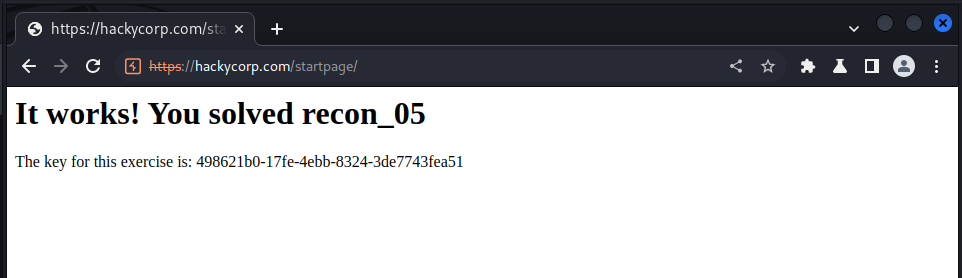
accessing the /startpage endpoint we got the following result:
Recon 06
This exercise covers default vhost
This challenge requires us to access the vhost, we do this by getting the ip address of the server using ping and use curl to get the content:
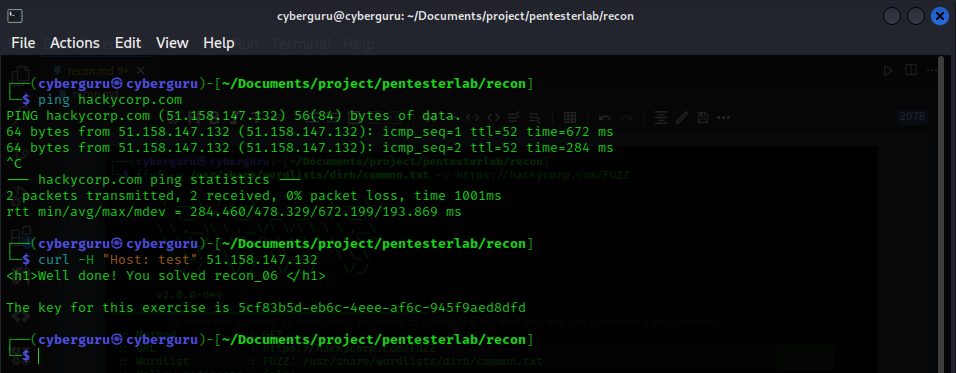
and we got the key !!!
Recon 07
This exercise covers default TLS vhost
Objective
For this challenge, your goal is to access the default virtual host (“vhost”) over TLS.
We use curl to get the key for this challenge by appending https at the beginning of the ip address and got the following result:
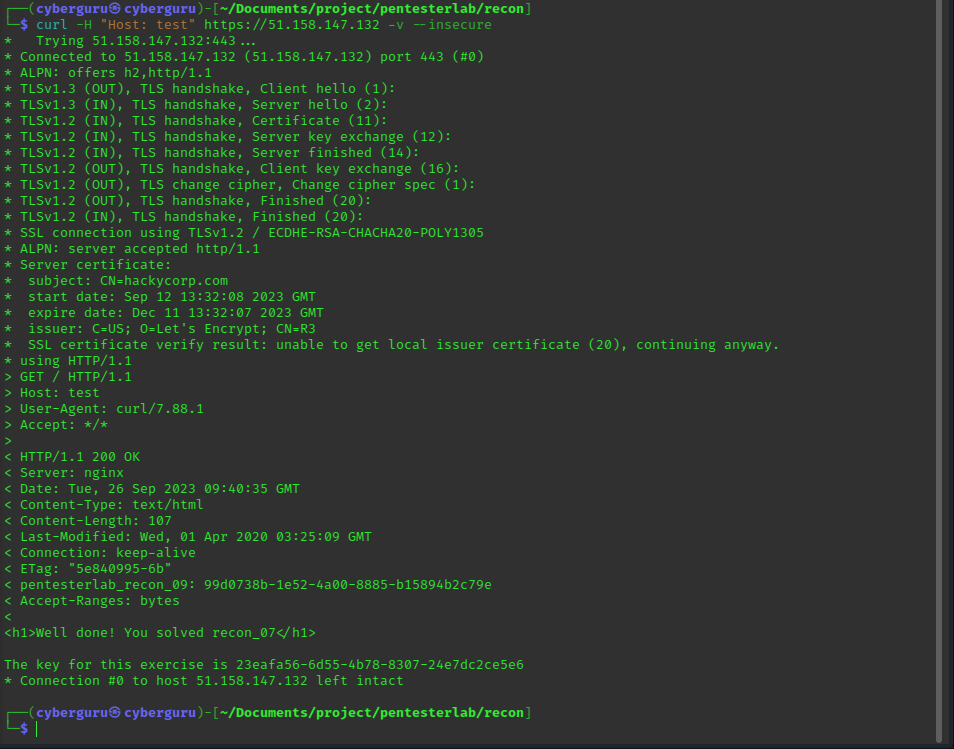
and yes we got the key !!!
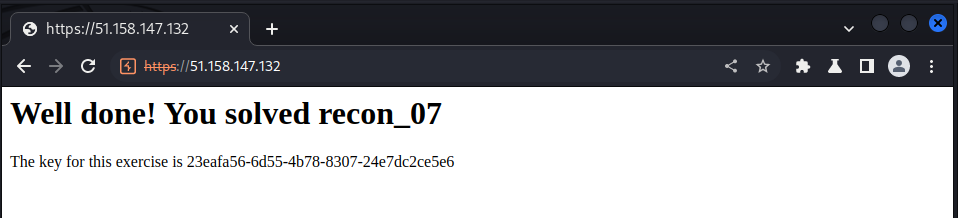
using the web view we could do the same:
Recon 08
This exercise covers aliases in TLS certificates
Objective
For this challenge, your goal is to access the alternative names in the certificate.
we use the alternative name in the TLS cert info located here:
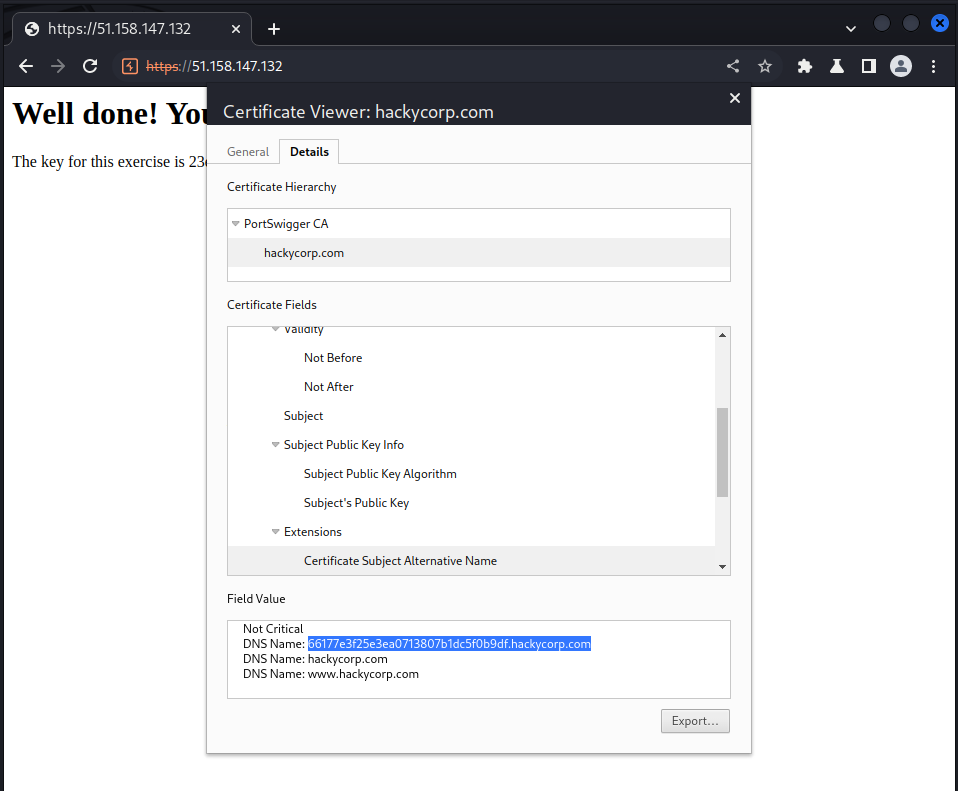
accessing this link gives us this:
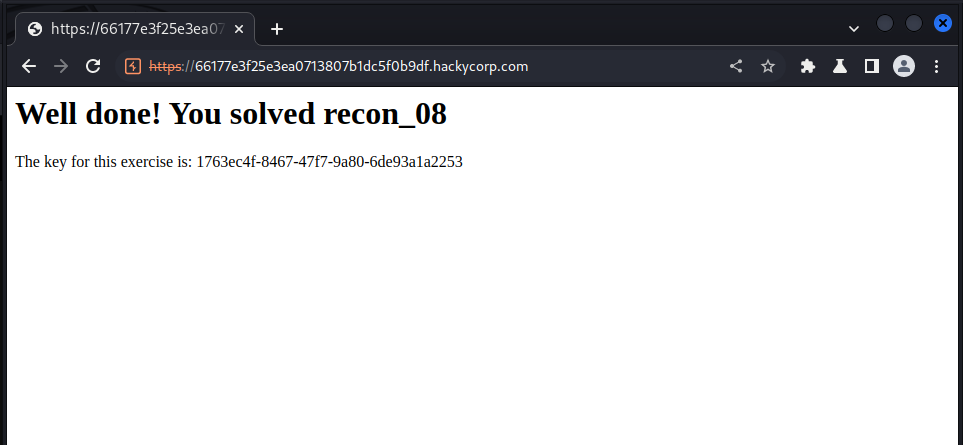
Now we’ve got the key!!!
Recon 09
For this lab, we observe the header for the key
we check the header of a request of the header: 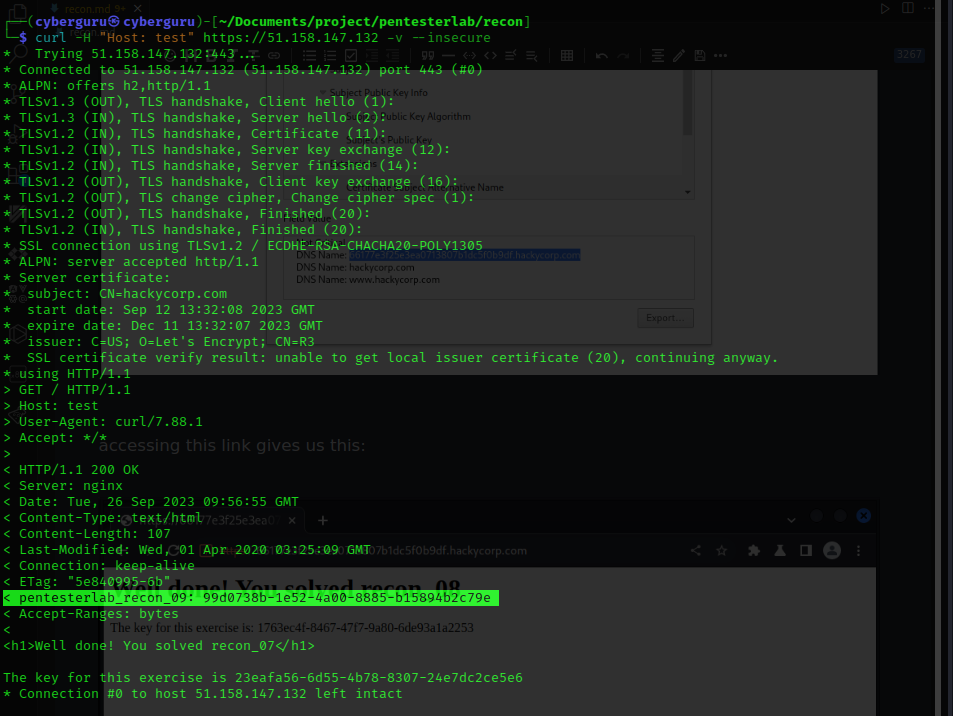
Key archived !!!!
Recon 10
This exercise covers visual content discovery
Objective
For this challenge, your goal is to use visual reconnaissance. You will need to find the website with the key in red.
For this challenge, the web applications are hosted under: 0x[“%02x”].a.hackycorp.com
first we generate a list of subdomain host using python:
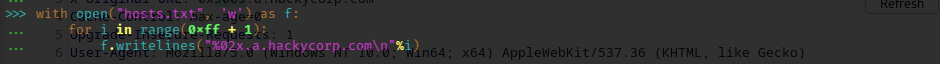
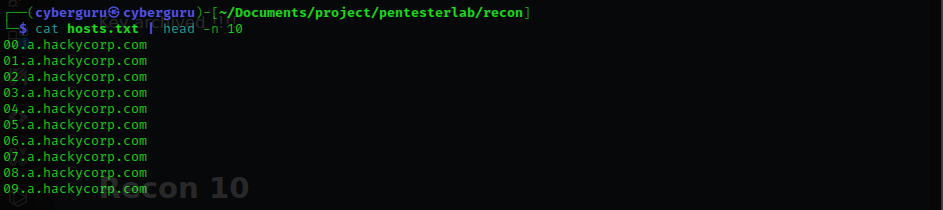
this content is written to a file, checking the first 10 items using head:
we now use curl to download all the pictures on each of this link:
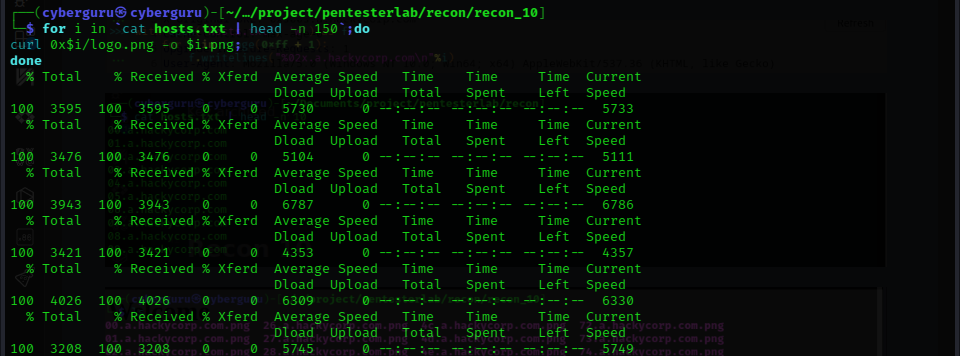
Result of downloaded file:
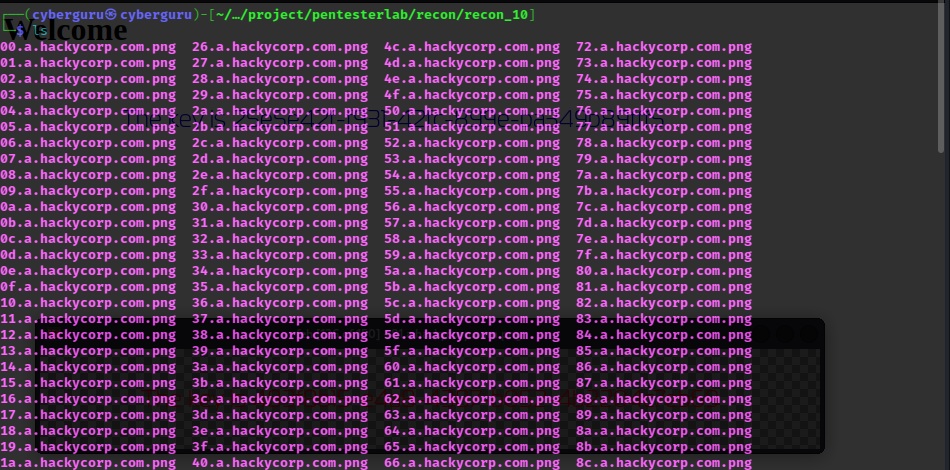
we now use feh to go through each of this file till we find the one in red:
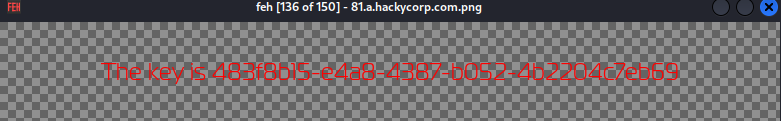
and that’s how we got the key!!!!!!!
Recon 11
Virtual host brute forcing
Objective
For this challenge, your goal is to brute a virtual host.
To accomplish this we use ffuf with the following parameters:
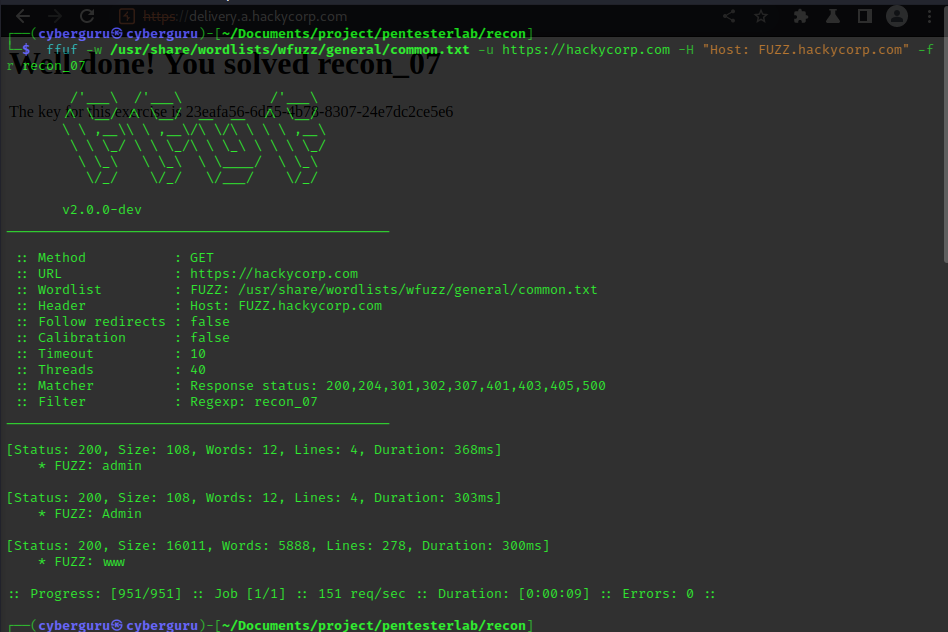
in the result we got admin, Admin and www; let’s try them out using curl:
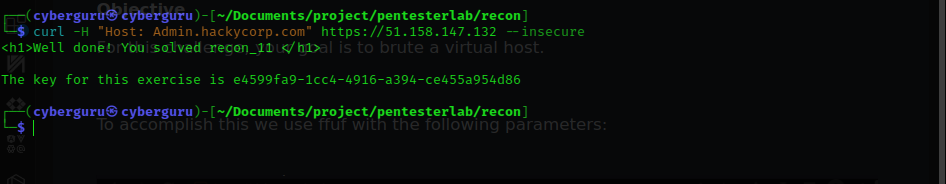
we got the key to this lab!!!
Recon 12
Objective
For this challenge, your goal is to access a load-balanced application hosted at the address balancer.hackycorp.com.
We simple use curl to get the key to this lab:
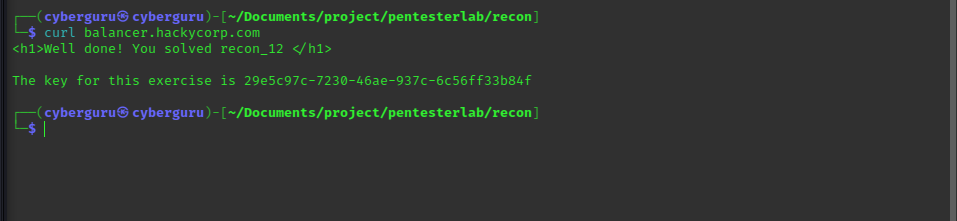
and there it is; the key 😄!!!
Recon 13
In this challenge, you need to find the TXT record linked to key.z.hackycorp.com
Objective
For this challenge, your goal is to retrieve the TXT record for key.z.hackycorp.com.
using the dig in bash we got:
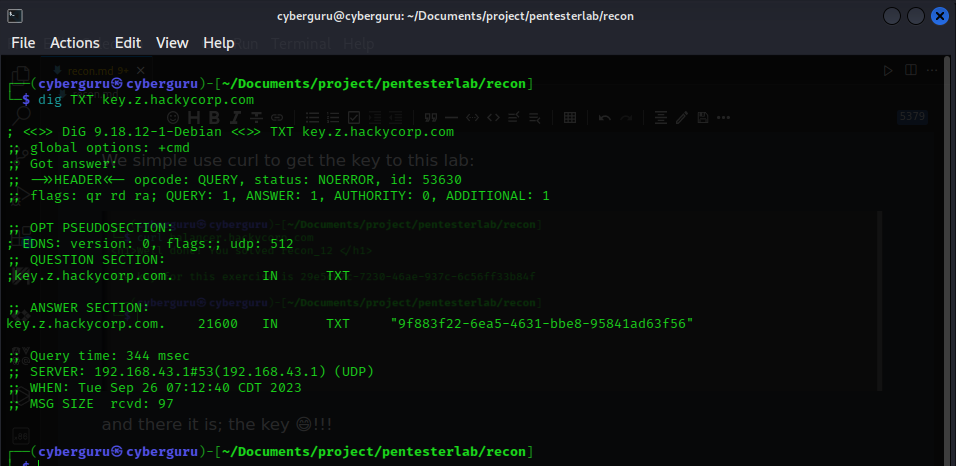
and in there lays the key!!!!
Recon 14
In this challenge, you need to find a TXT record by doing a zone transfer on z.hackycorp.com
Objective
For this challenge, your goal is to perform a zone transfer on z.hackycorp.com.
Recon 18
In this challenge, you need to look at the public repository of the developers in the organization
To solve this lab we need to perform a dns zone transfer and read the data that has been transferred which includes TXT, AAA, A records and so on, our key would be stored in the TXT record according to the lab description,
In the graphic below we perform a dns zone transer in asynchronous mode using the asynchronous mode (axfr) from ns1.hackycorp.com:
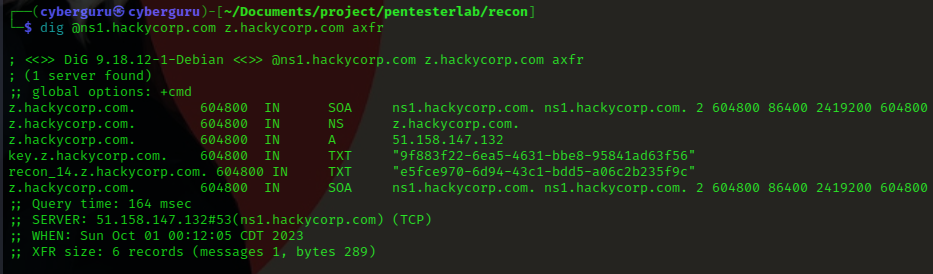
And there goes our key in the TXT record !!!
Recon 15
In this challenge, you need to find a TXT record by doing a zone transfer on the internal zone “int”
To perform an internal zone transfer we use the following command:
dig int [domain/ipaddress] axfr
running the command with the hackycorp address we have:
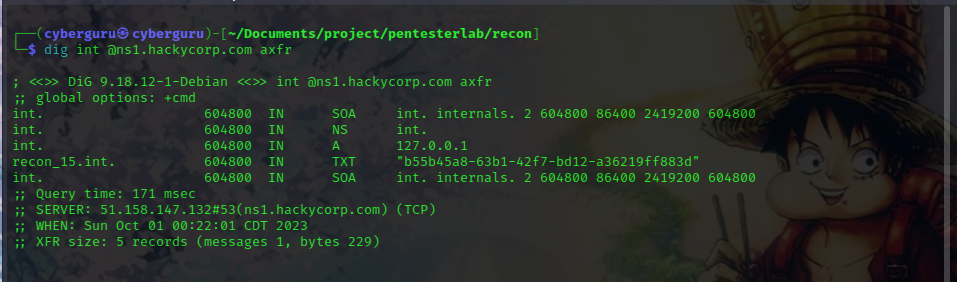
This gives us our key!!!
Recon 16
In this challenge, you need to find the version of Bind used
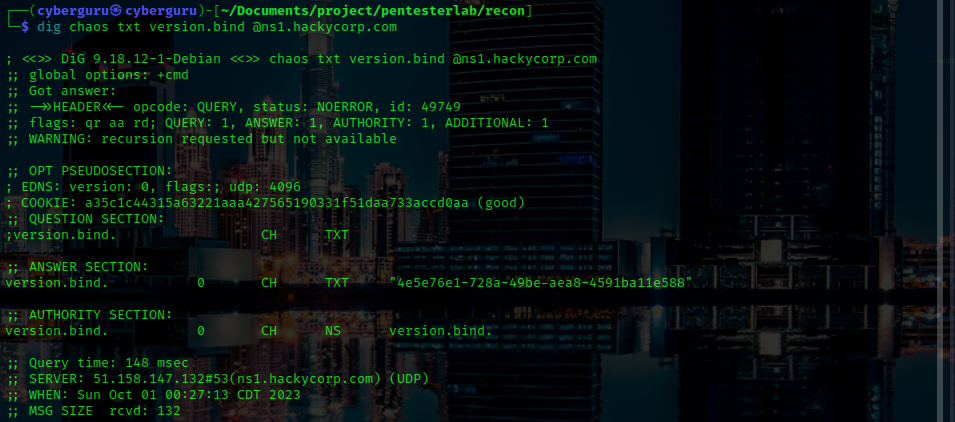
in this challenge we are to determine the version of bind use for the dns software.
first of all what is bind ?
BIND (Berkeley Internet Name Domain) is a software collection of tools including the world’s most widely used DNS (Domain Name System) server software. This feature-full implementation of DNS service and tools aims to be 100% standards-compliant and is; intended to serve as a reference architecture for DNS software.
To get the version of bind used we use the following command:
dig chaos TXT version.bind [ipaddress/domain]
Recon 17
In this challenge, you need to look at the name of the developer used in the repository test1
Objective
For this challenge, your goal is to look at the name of the developer who committed code for the organization in the repository test1 on Github (you will need to find the Github account for Hackycorp first).
To solve this lab we do as the challenge suggested, we first find the Hackycorp github account on github:
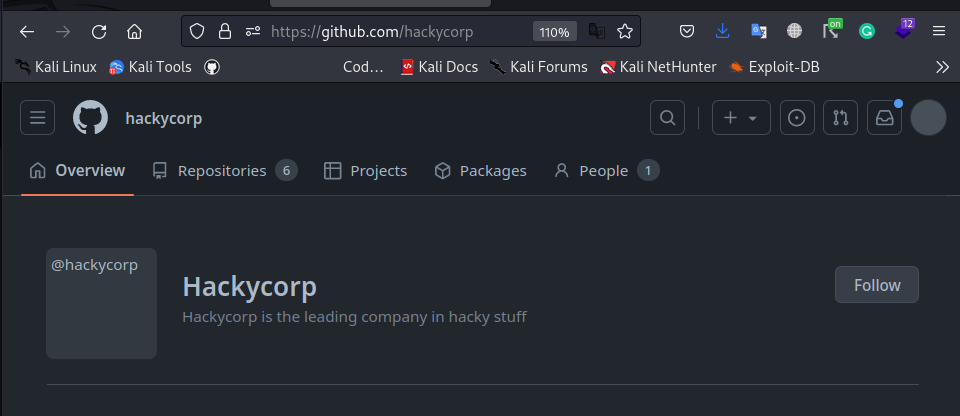
Then we look for test1 repo and check the developer’s name:
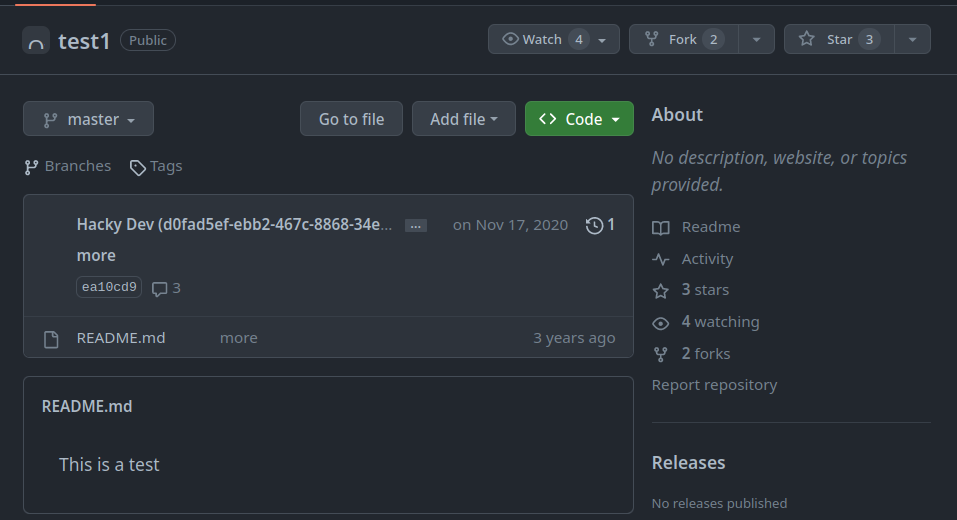
Recon 18
In this challenge, you need to look at the public repository of the developers in the organization
Objective
For this challenge, your goal is to look at the public repository of the developers of the organization.
As the challenge objective specifies, we check the developers existing in the hackycorp company account and saw only one, we navigate to this account and check all their repo, and we come across this:
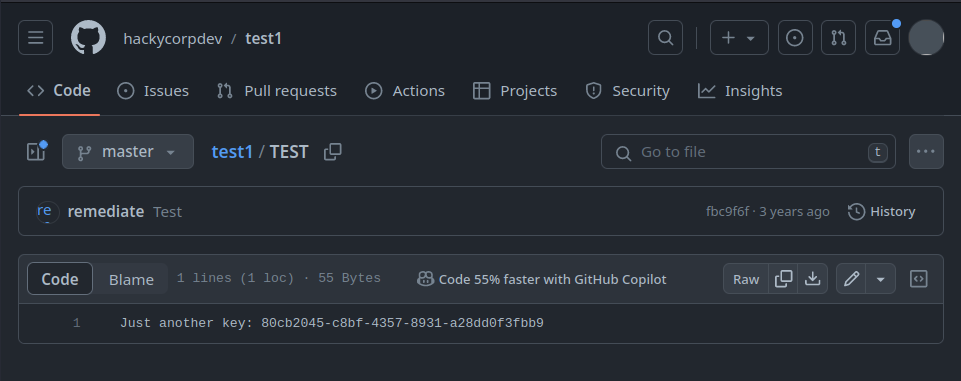
Yay, 😆 we got our key !!
Recon 19
In this challenge, you need to look at the email addresses used for commits in the repository repo7
Objective
For this challenge, your goal is to look at the repository repo7 and find an email address that is not like the other one.
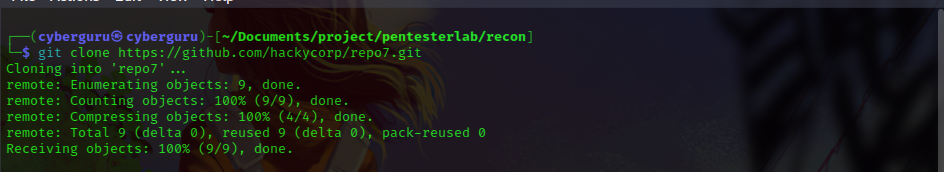
To solve this lab we clone the repo7 repository
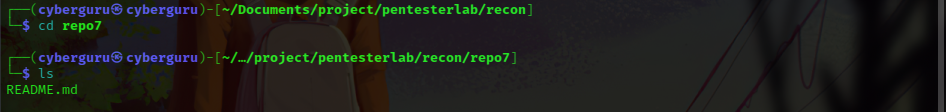
and navigate into the dir, then we use the command:
git log
this command reveals all commit details including the email of the developer and hash of each commit done
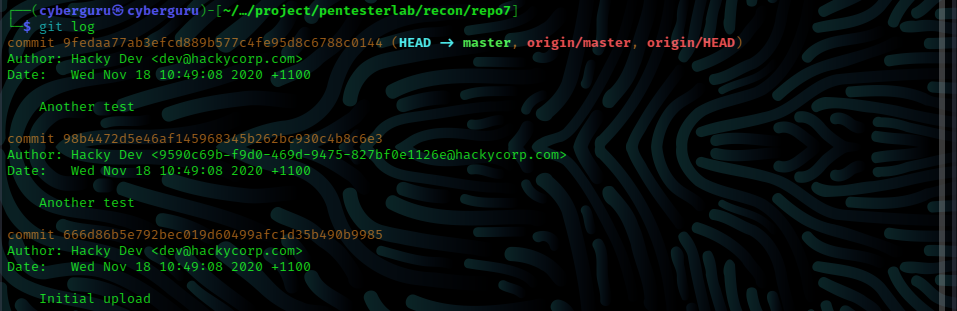
and with this we get the key in the 2nd entry.
Recon 20
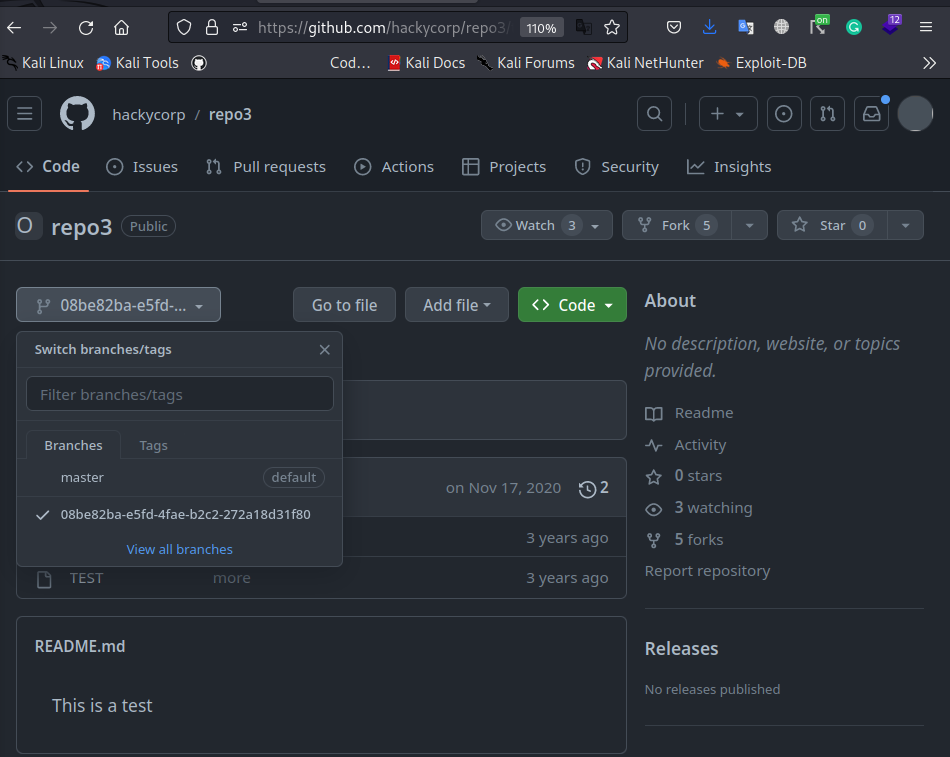
In this challenge, you need to look at the branches in repo3
Objective
For this challenge, your goal is to look at the repository repo3 and check different branches.
To solve this lab we simply need to list all branches existing in repo3, we navigate to the hackycorp company account and do just that
Recon 21
In this challenge, you need to look at the information in the branches for repo4
Objective
For this challenge, your goal is to look at the repository repo4 and check different branches.
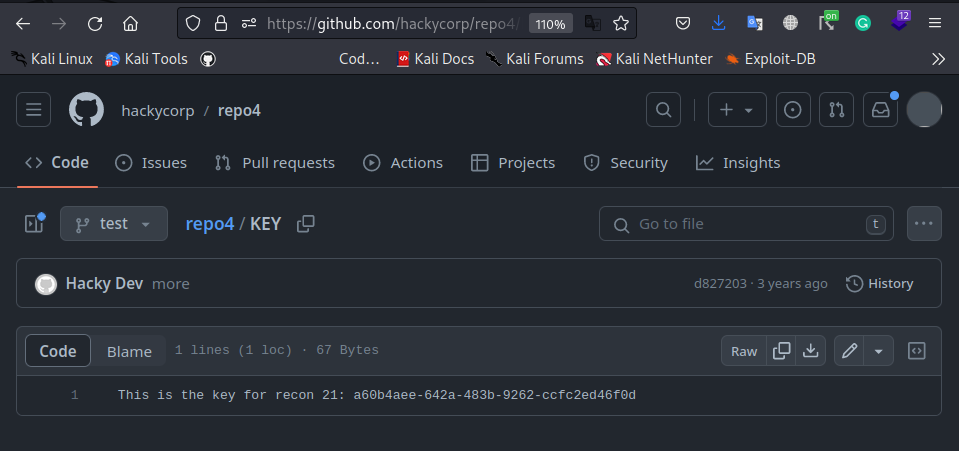
To solve this lab, we navigate to repo4 in the hackycorp repos, then we check on the test branch:
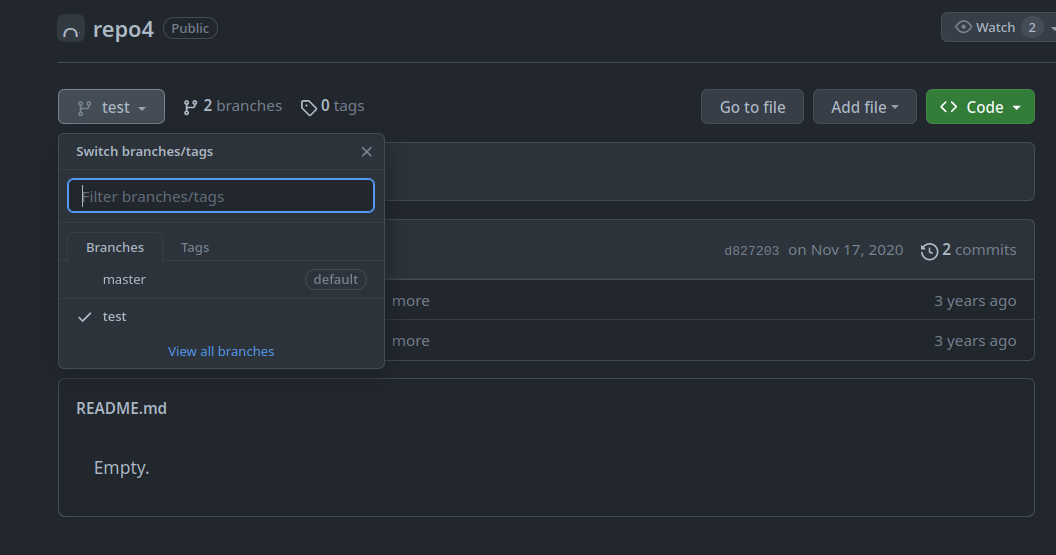
In the test branch there exist a file called KEY which contains our desired key:
Recon 22
In this challenge, you need to look in repo9 for deleted files
Objective
For this challenge, your goal is to find a file that has been deleted in repo9.
To solve this lab, we first navigate to the repo9, then simply have to find a file that has been deleted in commit history; going through the commit history we stumble across this:
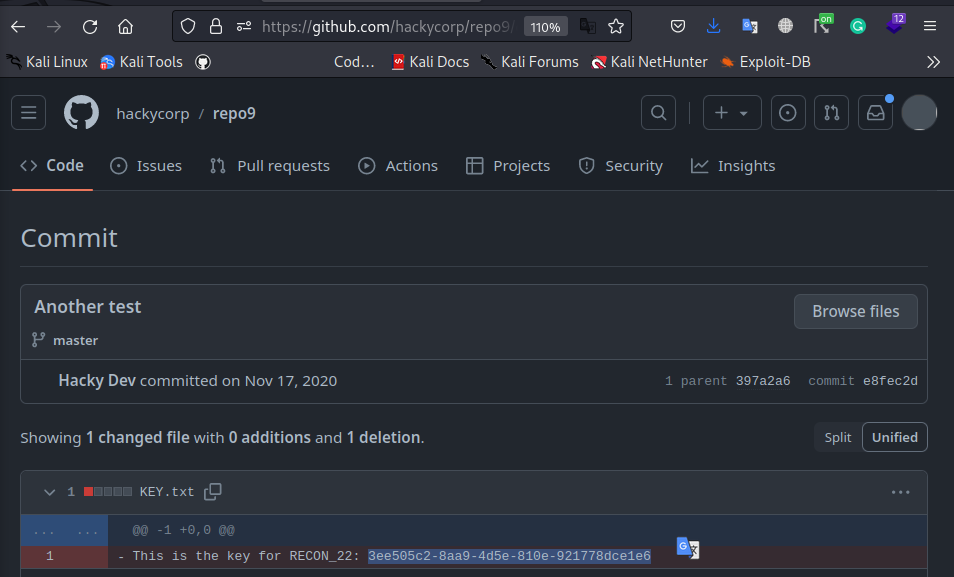
and this gives us our key!!!
Recon 23
In this challenge, you need to look for sensitive information in commit messages
Objective
For this challenge, your goal is to look at the repository repo0a and find sensitive information in the commit message.
As the challenge objective stated we navigate to the repo and check the commit with more comments:
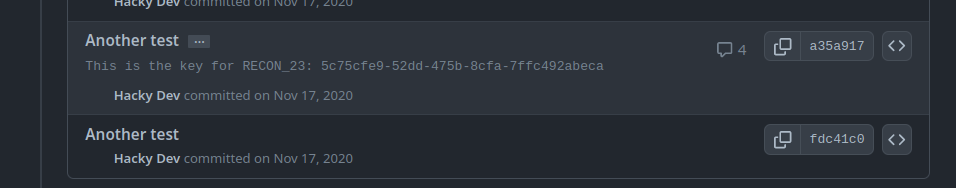
And this gives us our KEY!!!
Recon 24
In this challenge, you need to look for a file named key.txt in the place used to serve the assets for the main website
Objective
For this challenge, your goal is to look at the server used to load assets (JavaScript, CSS) and find a file named key.txt.
To solve this lab, we simply check the assets link from view-source page and end the path with key.txt:
assets.hackycorp.com/key.txt
Result:
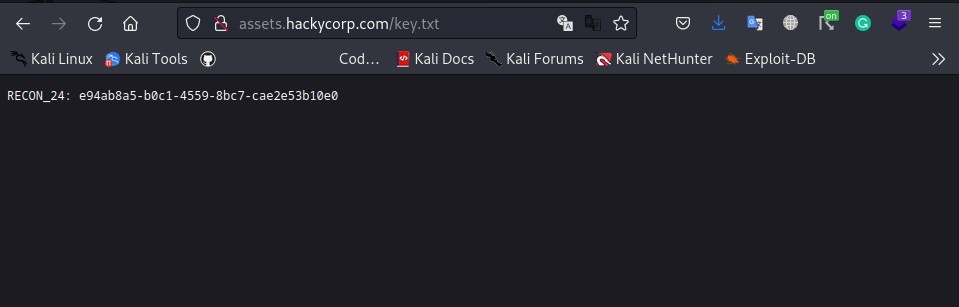
and this gives us the key!!!
Recon 25
In this challenge, you need to look for a file named key2.txt in the place used to serve the assets for the main website
Objective
For this challenge, your goal is to look at the server used to load assets (JavaScript, CSS) and find a file named key2.txt. However, this time you will need to be logged in to access it.
Amazon Web Services Storage Service (S3) allows file owners to set permissions on files. Historically, the rules “Any users” wasn’t well explained and lead a lot of people to think only people in their
Amazon account could access a file. However, this was allowing any AWS account to access the file.
To solve this lab we need an AWS account to view the key2.txt file, this is due to improper file permission set on files in AWS S3 buckets, that allows any AWS account to be able to view unrestricted permission files
we do this and got our key
Don’t have an AWS account, so we used an alternative from a friend 😆 !!!!
Recon 26
In this challenge, you need to look for a key in the JavaScript used by the website
Objective
For this challenge, your goal is to look at the server used to load assets (JavaScript, CSS) and find a hard coded key in one of the JavaScript files.
To solve this lab we extracted all the JS extension file in the view-source page and navigate through them in search for recon_29 and sure enough we came across it in script.js:
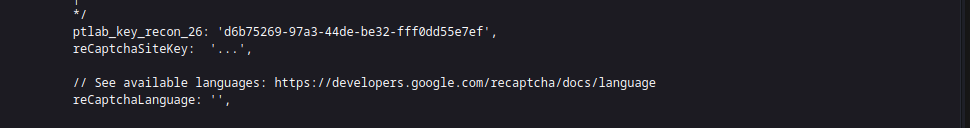
and we got our key hard coded within a comment 😆
This marks the end of the recon challenge !!!!